
Protect your clients from evolving cyber threats with a comprehensive security solution. Leverage advanced detection mechanisms, robust authentication protocols, and real-time security insights all in one place. Proactively address potential risks and ensure a secure IT environment for your clients, empowering them to focus on their business goals.

General Features
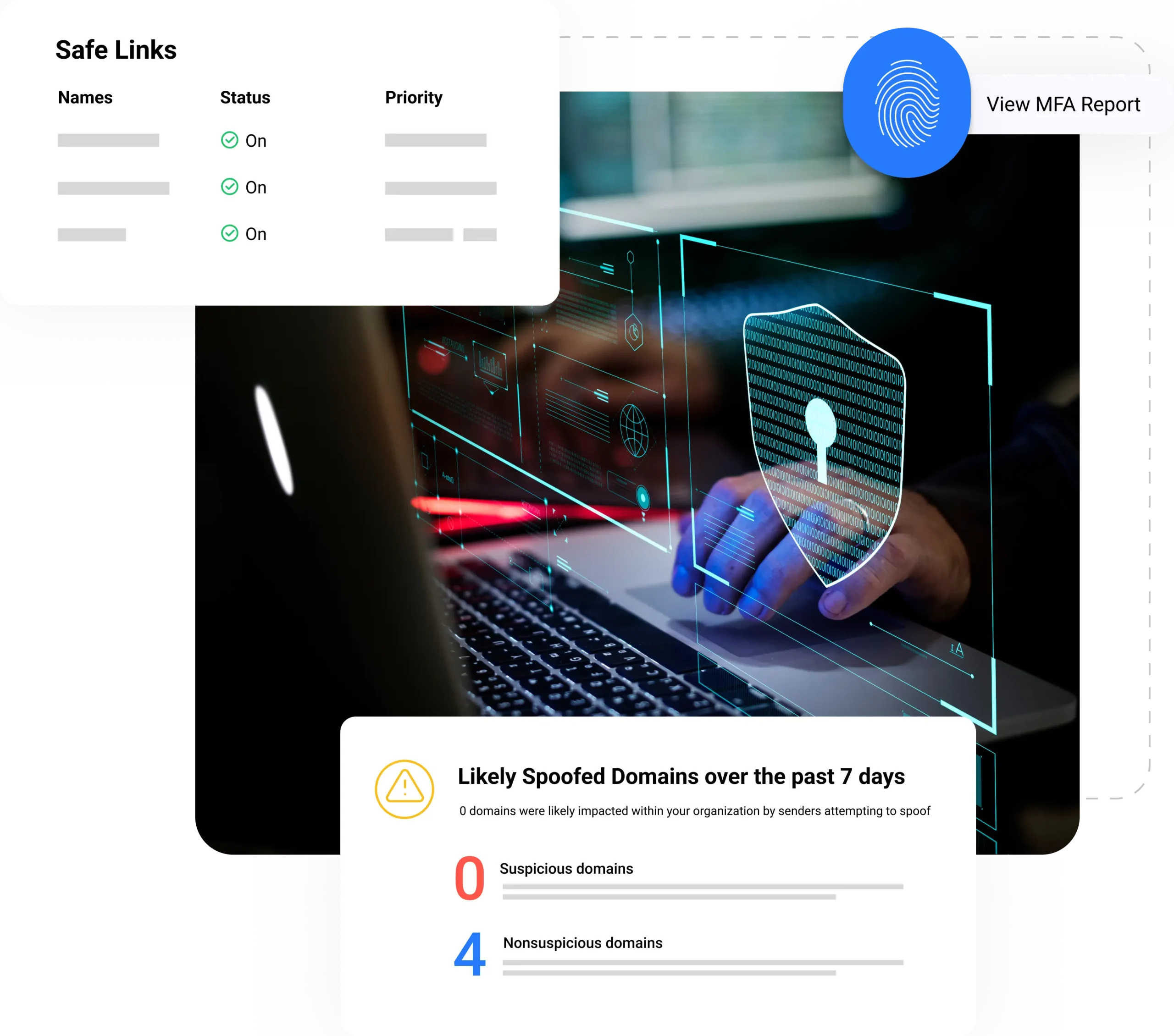
Security compliance is critical in today’s complex IT landscape. MSPControl empowers you to deliver top-tier compliance and protection through a comprehensive solution that combines advanced detection mechanisms, robust authentication protocols, and real-time security insights—all within a single, unified platform. Proactively identify and mitigate potential risks before they escalate, ensuring your clients’ IT environments meet the highest security compliance standards.

MSPControl: The all-in-one platform that empowers managed service providers to deliver comprehensive, proactive, and reliable security compliance solutions to their clients—ensuring unwavering peace of mind.

No credit card required for free, limited license.
