Hosted Organization Policies
The Hosted Organization Policies section in MSPControl defines policy-driven configuration and automation rules that apply to hosted organization (tenants). These settings allow administrators to standardize provisioning, retention, backup, mailbox rules, and security behavior across multiple hosted environments integrated with Microsoft 365, Exchange Online, SharePoint, and Azure services.
Table of Contents
Global Exchange Mailbox Plans
The Global Exchange Mailbox Plans section allows administrators to define standardized mailbox configurations with specific size quotas, protocol settings, retention behavior, and archiving options. These plans help standardize mailbox provisioning and ensure compliance across tenants.
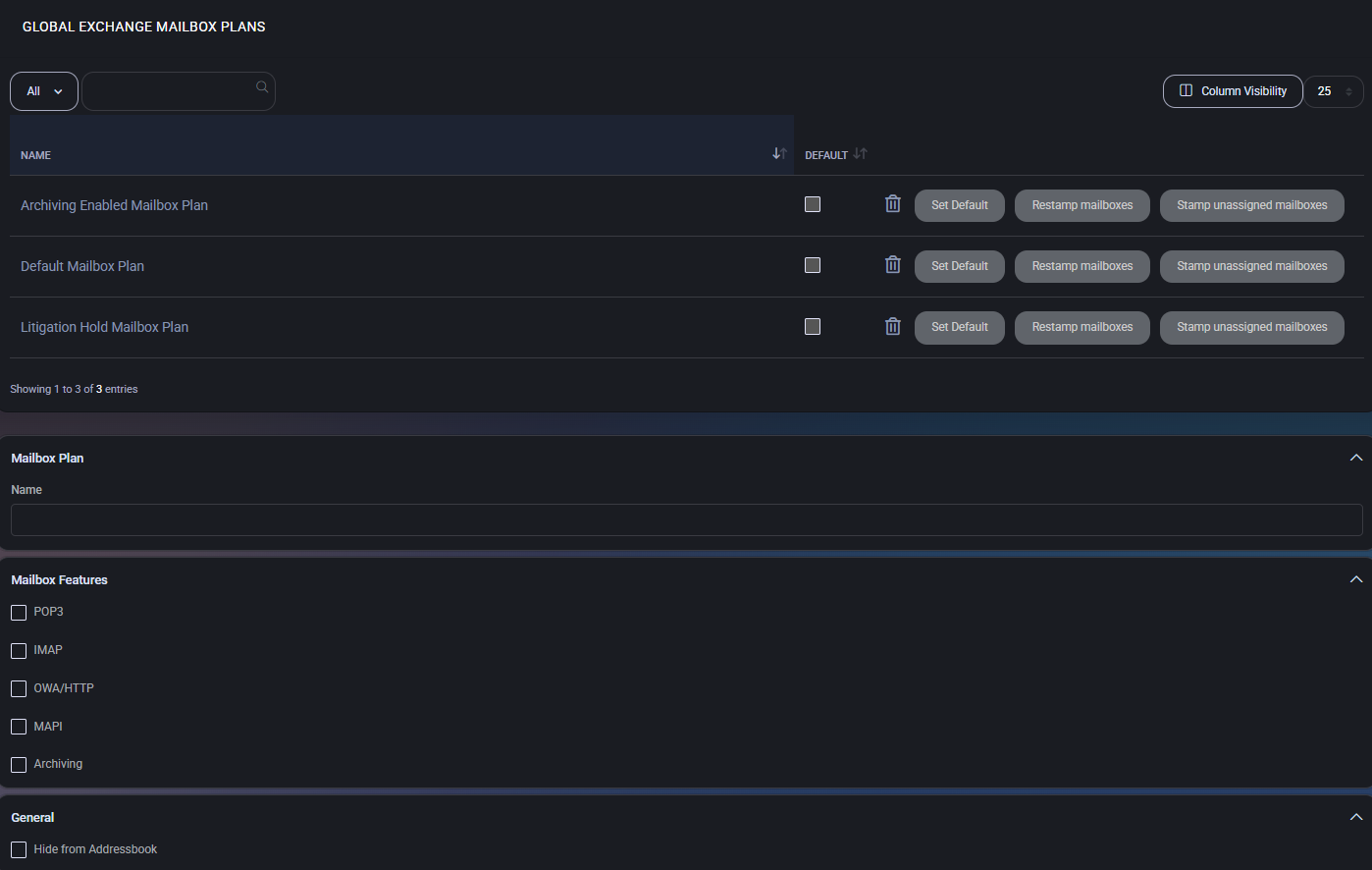
Mailbox Plans Table
The mailbox plans list displays all defined plans. Each plan includes:
- Set as Default: The plan will be used automatically during mailbox creation if no other plan is specified.
- Restamp Mailboxes: Applies the current plan settings to all already assigned mailboxes.
- Stamp Unassigned Mailboxes: Applies this plan to mailboxes that currently have no assigned plan.
Create or Edit Mailbox Plan
Clicking Add New or editing an existing plan opens a configuration panel with the following sections:
Mailbox Features
- POP3 / IMAP / OWA / MAPI: Toggle to enable or disable each protocol independently.
- Archiving: Enables the built-in archive mailbox for this plan.
- Hide from Addressbook: Prevents the mailbox from being listed in the GAL (Global Address List).
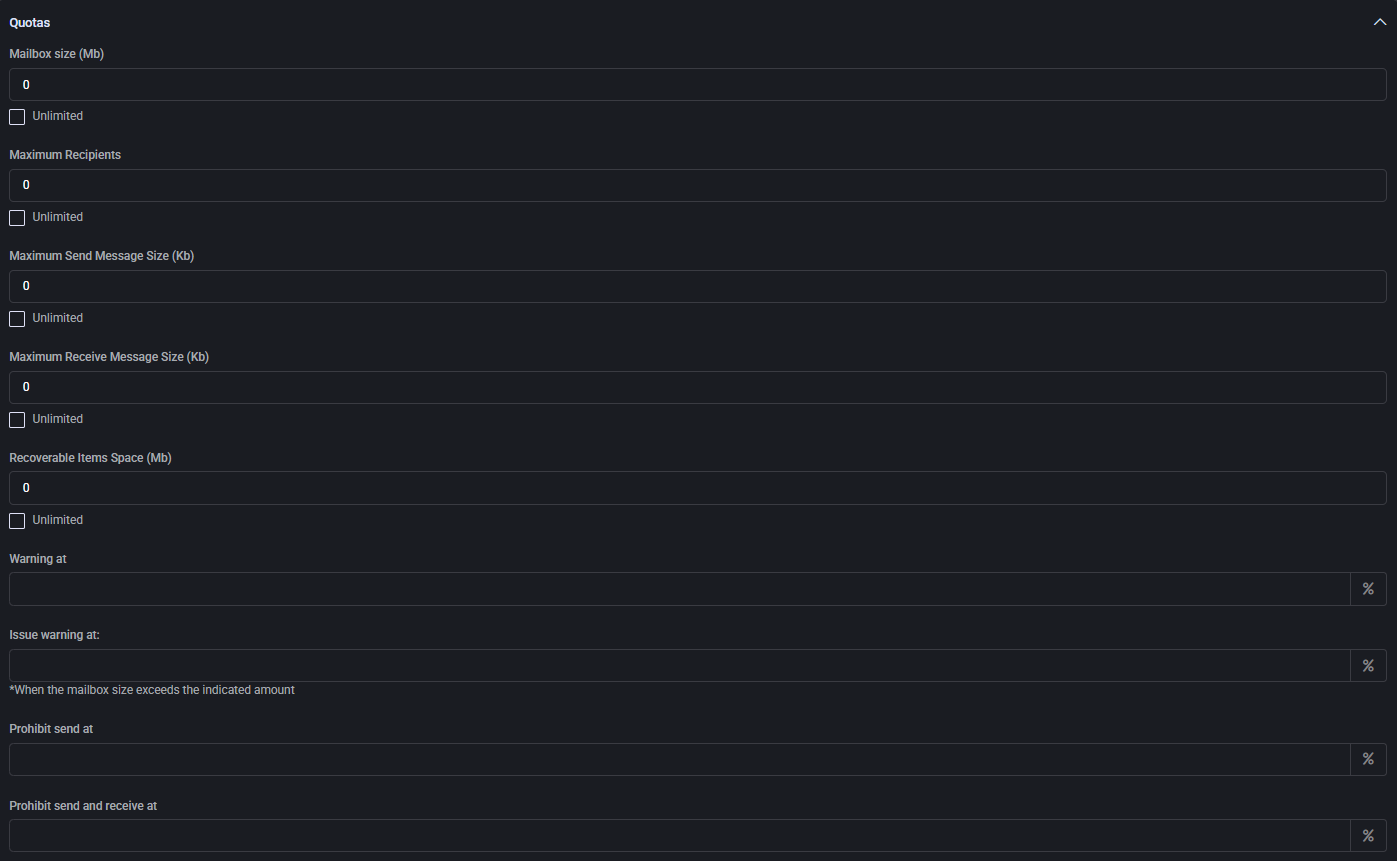
Quotas
Define mailbox capacity and messaging limits:
- Mailbox size (MB): Total storage quota for the mailbox.
- Maximum recipients: Limit of recipients per email message.
- Send/Receive size (KB): Maximum allowed size for incoming and outgoing emails.
- Recoverable items space (MB): Storage for recoverable or deleted items.
- Warning thresholds:
- Warning users
- Issuing official warnings
- Blocking send
- Blocking send and receive
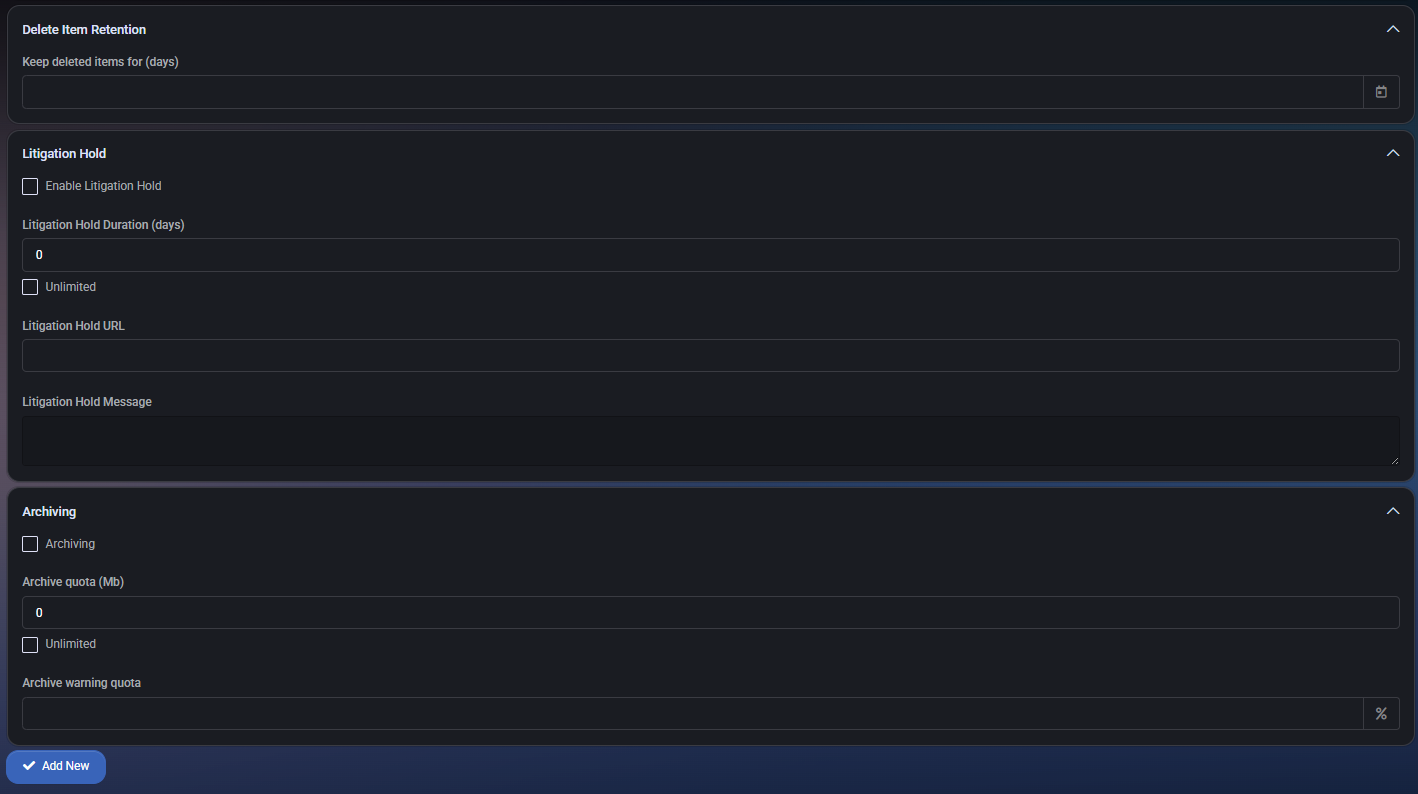
Delete Item Retention
- Keep deleted items for (days): Specifies the retention period before deleted items are permanently removed.
Litigation Hold
- Enable Litigation Hold: Locks mailbox data to comply with legal hold requirements.
- Litigation Hold Duration: Number of days to preserve content (or select unlimited).
- Litigation Hold URL: Optional link to compliance documentation or policy.
- Litigation Hold Message: Optional custom message for compliance display.
Archiving
- Archive quota (MB): Total storage limit for the archive mailbox.
- Archive warning quota: Warning threshold to notify when nearing archive quota.
Best Practices
- Create specific mailbox plans for each business tier (e.g., Basic, Business, Compliance).
- Use the default flag for automatic mailbox plan selection during provisioning.
- Apply Restamp only when you need to synchronize updated plan values to existing mailboxes.
- Enable Litigation Hold only when legally required — it prevents deletion but can increase storage costs.
- Use mailbox quotas conservatively to avoid over-allocation and support Exchange Online limits.
Global Retention Policy
The Global Retention Policy section allows you to define centralized mailbox retention settings that apply across the tenant. These policies manage how long data is kept before being automatically deleted, ensuring compliance and storage optimization.
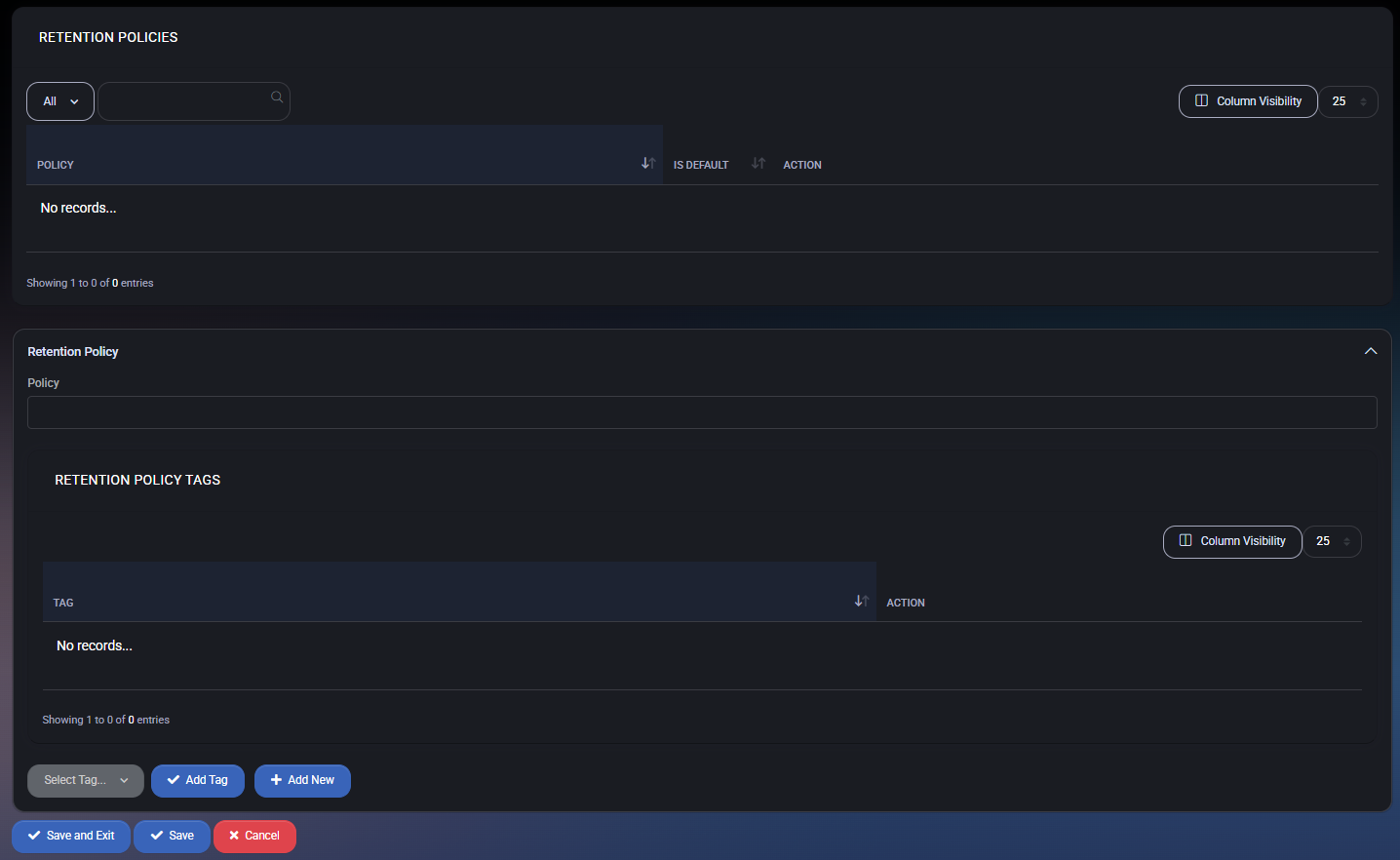
Retention Policies Table
This section displays all configured retention policies. Each policy can be set as default and contains associated retention tags.
- Policy Name: Identifier for the retention policy.
- Is Default: Marks the policy as the default applied to new mailboxes or plans.
- Action: Allows editing or deleting the policy.
Create or Edit Retention Policy
Clicking Add New or editing an existing policy opens the configuration panel with the following fields:
- Policy: Enter a unique name for the retention policy.
Retention Policy Tags
Each policy contains a set of tags defining specific retention actions (e.g., delete after X days, archive, etc.).
- Tag: Descriptive name for the retention action.
- Action: Controls for editing or removing the tag from the policy.
- Select Tag: Use the dropdown to choose from existing tags.
- Add Tag: Attach the selected tag to the policy.
- Add New: Create a brand new retention tag directly from this panel.
Best Practices
- Use a default retention policy to apply basic compliance rules globally.
- Organize tags based on mailbox types (e.g., inactive, shared, project-based) to better manage data lifecycle.
- Define short-term and long-term retention tags to separate operational and compliance requirements.
- Always review tag impact before assigning them globally — especially if the tag includes permanent deletion.
Global Retention Policy Tag
The Global Retention Policy Tag section allows administrators to define specific retention rules for different mailbox folders and item types across hosted tenants. These policy tags determine how long emails or items are retained and what action should be taken after the retention period expires.
Policy Tags can be created and added to a Global Retention Policy for centralized enforcement. Tags can target individual folders or apply globally to all mailbox content.
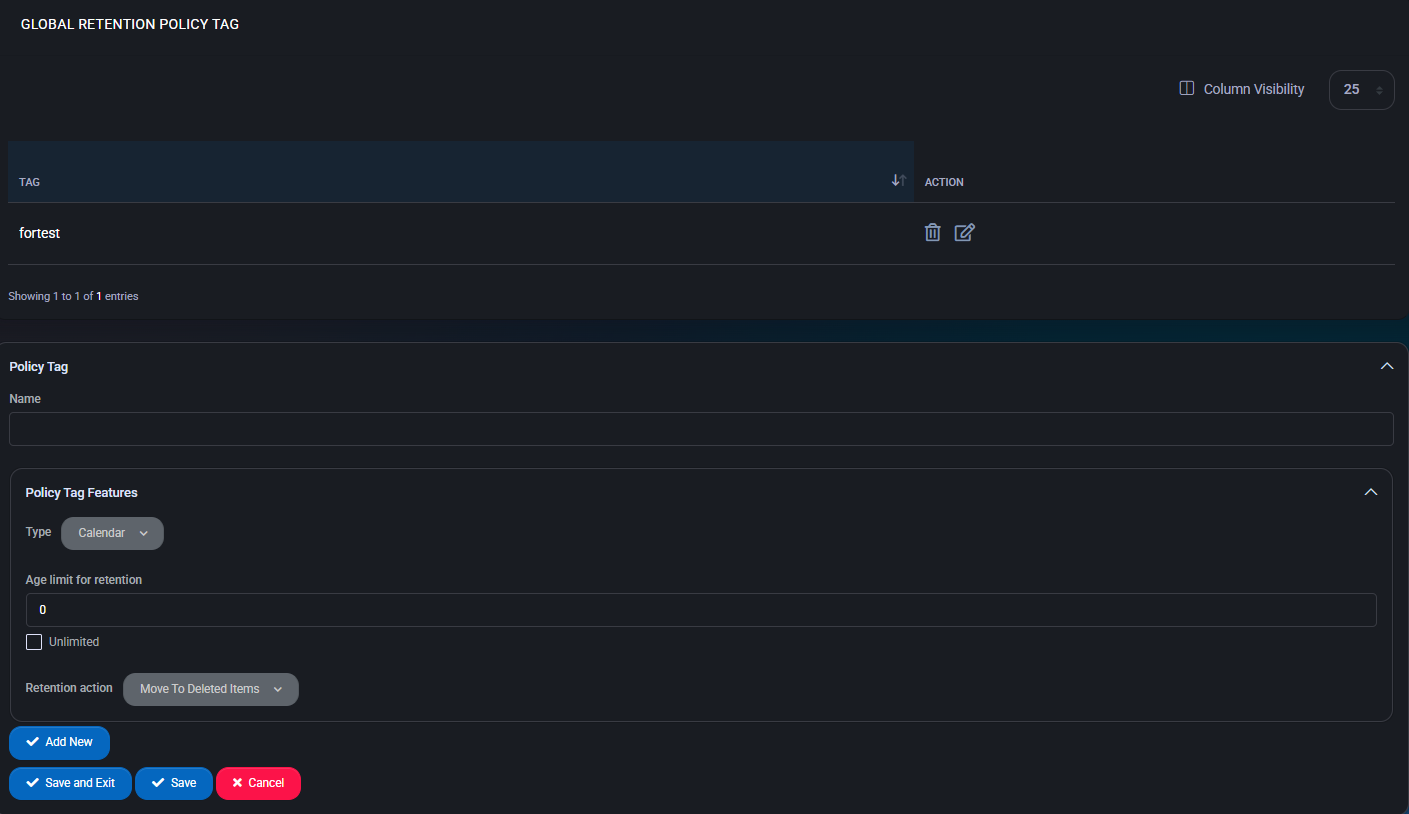
Policy Tag Fields
- Name: Identifier for the retention tag.
- Type: Folder or item type the tag applies to. Options include:
- Calendar, Contacts, Deleted Items, Drafts, Inbox, Junk Email, Journal, Notes, Outbox, Sent Items, Tasks
- All (global), Managed Custom Folder, Rss Subscriptions, Sync Issues, Conversation History, Personal, Recoverable Items
- System folders like Non Ipm Root or Legacy Archive Journals
- Age Limit for Retention: Number of days before the tag’s action is triggered.
- Unlimited: Checkbox to override age limit and retain items indefinitely.
- Retention Action: Defines what happens when the age limit is reached. Options include:
- Move to Deleted Items
- Move to Folder
- Delete and Allow Recovery
- Permanently Delete
- Mark as Past Retention Limit
- Move to Archive
Best Practices
- Use folder-specific tags for granular retention control (e.g., apply longer retention for Inbox vs. Junk).
- Prefer the “Move to Archive” action to support compliance without permanent deletion.
- Set global retention tags only when all mailbox content must be uniformly processed.
- Ensure tag names clearly indicate their purpose and duration for future reference.
- Periodically audit existing tags and their usage across policies to avoid outdated rules.
Global Mailbox Rules
The Global Mailbox Rules section allows administrators to define rules that are applied to all user mailboxes within the system. These rules can automate actions such as moving, forwarding, deleting, or categorizing messages based on specific conditions and exceptions. They help enforce consistent behavior across hosted tenants and support operational or compliance-related workflows.
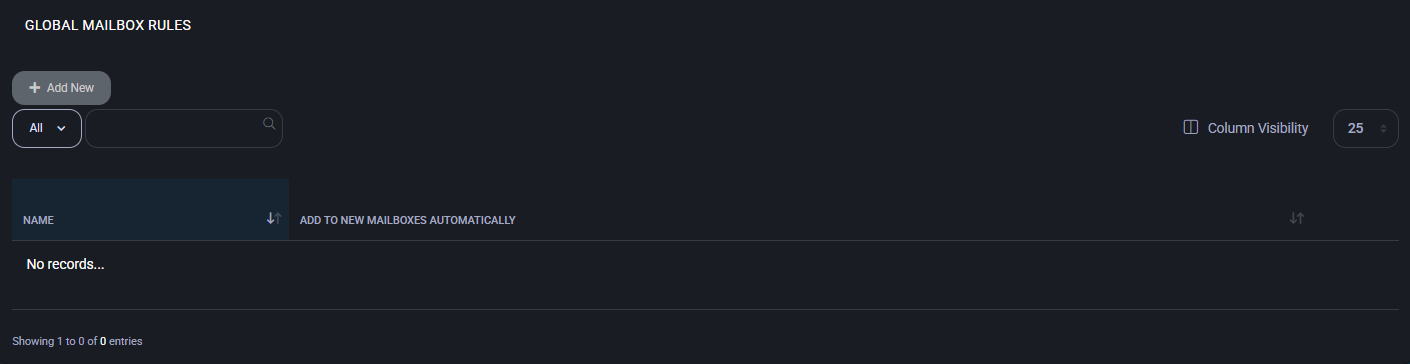
Global Mailbox Rules Table
This table lists all existing global rules configured in the system.
- Name: The rule’s name for identification and management purposes.
- Add to New Mailboxes Automatically: Indicates whether the rule is auto-applied to new mailboxes.
- Action: Provides options to edit or delete the rule.
Create or Edit Global Mailbox Rule
Clicking Add New or editing an existing rule opens a multi-section form:
General
- Name: The display name for the rule.
- Add to New Mailboxes Automatically: If enabled, this rule will apply to all future mailboxes.
- Comments: Optional field for internal notes or description.
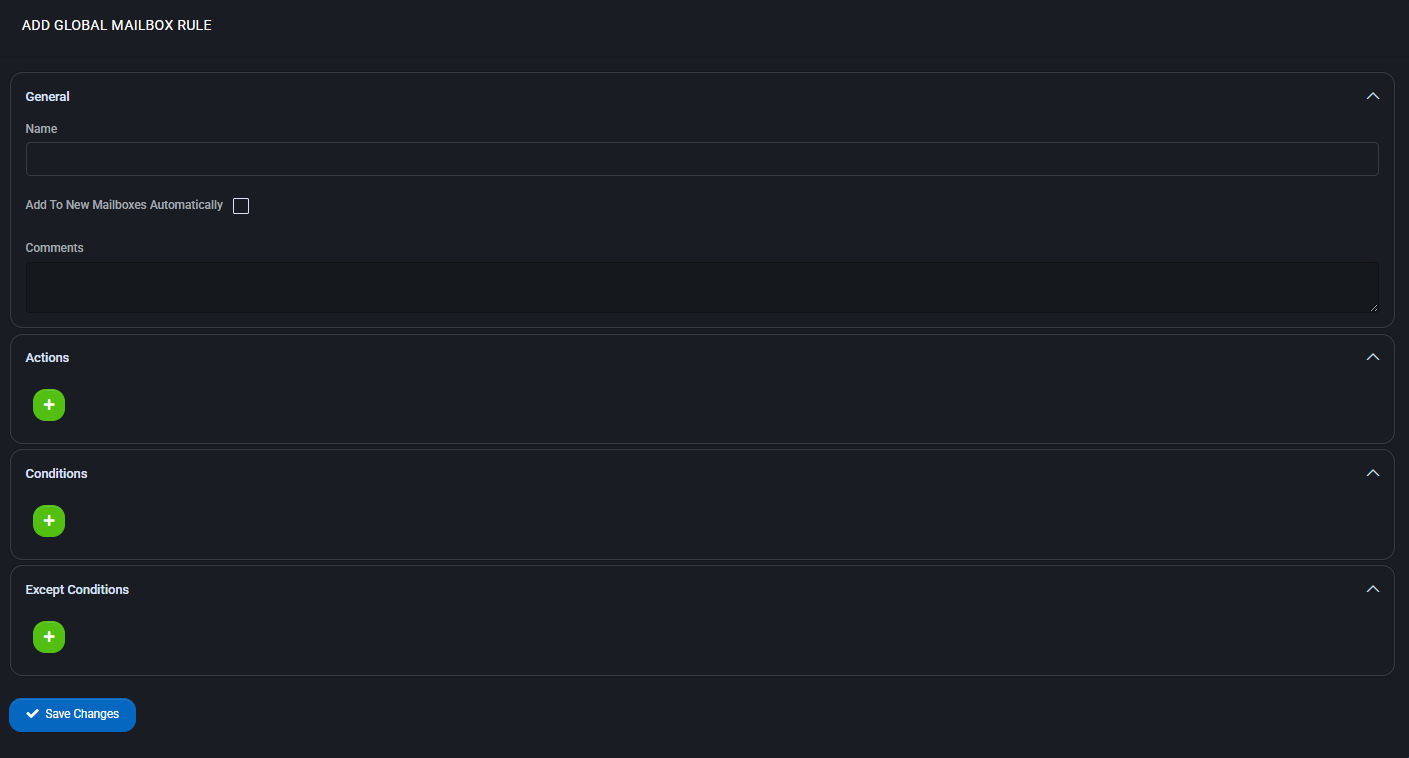
Actions
Add one or more actions that define what to do when the rule conditions are met. Available actions include:
- Apply Category
- Apply System Category
- Copy to Folder
- Delete Message / Delete System Category
- Forward To / Forward as Attachment To
- Mark as Read / Mark Importance
- Move to Folder / Pin Message
- Redirect To
- Stop Processing Rules
Conditions
Define the triggers for the rule using one or more conditions. Supported conditions include:
- Subject, Body, or Header Contains Words
- From / To / CC / BCC addresses and variations
- Received or Sent dates
- Message type, sensitivity, importance
- Attachment presence, classification, or size
Except Conditions
These exceptions allow the rule to skip certain messages even if they match the conditions. Available options mirror those in the Conditions section.
Best Practices
- Use clear and descriptive names for rules to simplify future auditing and maintenance.
- Apply rules automatically to new mailboxes for consistent policy enforcement.
- Use multiple conditions to narrow the scope and avoid misclassification or over-processing.
- Combine “Stop Processing Rules” with high-priority rules to prevent unintended execution of lower-priority ones.
- Thoroughly test rules before wide deployment, especially those that delete or forward messages.
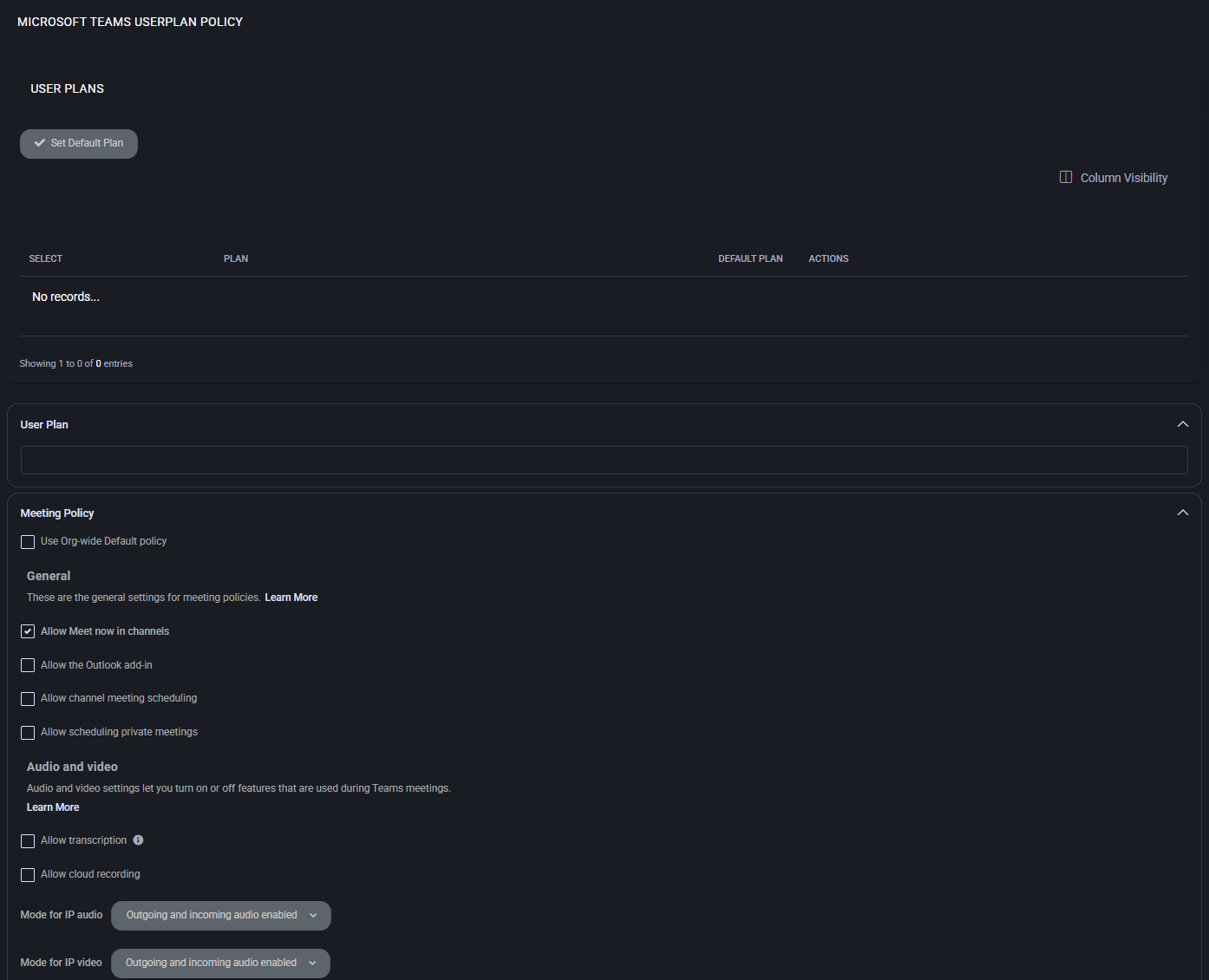
Microsoft Teams Userplan Policy
The Microsoft Teams Userplan Policy section allows administrators to configure meeting behavior for Microsoft Teams users across hosted tenants. Each user plan determines which features are available during meetings, such as screen sharing, chat, audio/video settings, participant controls, and scheduling permissions.
User plans help enforce consistent collaboration rules across an organization, enabling tailored policies per user group while supporting tenant-wide defaults.
User Plans Table
This table lists all Microsoft Teams user plans configured in the system. Each plan defines specific Teams meeting policies for different users or user groups.
- Set Default Plan: Marks a selected plan as the default policy applied to all users unless overridden manually.
- Plan List: Displays the available plans along with their assigned status and actions.
- Actions: Use the corresponding action buttons to edit or remove plans.
Meeting Policy – Audio and Video
These options control the availability of audio and video features in Microsoft Teams meetings.
- Allow IP video: Enables or disables the ability for users to transmit video during meetings.
- Allow NDI streaming: Allows the use of NDI® (Network Device Interface) technology for broadcasting Teams meetings. Useful for advanced streaming setups.
- Media bit rate: Sets the maximum media bitrate in kilobits per second (Kbps) for audio/video streams. Default is
5000.
Meeting Policy – Content Sharing
Defines what types of content users can share during Teams meetings.
- Screen sharing mode: Sets the screen sharing permission. Options include:
Single application: Share only a selected application window.Entire screen: Allows sharing the whole desktop.
- Allow a participant to give or request control: Enables shared control between participants during screen sharing.
- Allow an external participant to give or request control: Same as above but for users outside the organization.
- Allow PowerPoint sharing: Allows sharing PowerPoint presentations natively.
- Allow whiteboard: Enables access to Microsoft Whiteboard during meetings.
- Allow shared notes: Enables the use of shared OneNote notes during meetings.
Meeting Policy – Participants and Guests
Controls how external users, guests, and anonymous participants can join and interact during meetings.
- Let anonymous people start a meeting: Allows users without accounts to initiate a meeting (if enabled).
- Roles that have presenter rights in meetings: Defines who has presenter privileges:
Everyone, but user can override: Default option allowing all attendees to be presenters, but users can change this in meeting settings.
- Automatically admit people: Defines who bypasses the lobby automatically. Options include:
Everyone in your organization: Only internal users skip the lobby.
- Allow dial-in users to bypass the lobby: Determines whether PSTN (phone-based) users can join directly without waiting in the lobby.
- Allow Meet now in private meetings: Enables users to start ad-hoc (Meet now) meetings in private contexts.
Meeting Policy – Accessibility and Chat
- Enable live captions: Enables automatic transcription of speech during meetings.
Disabled but the user can override: Captions are disabled by default, but end users can enable them manually.
- Allow chat in meetings: Controls chat functionality availability during meetings.
Enabled: Chat is available to all participants.
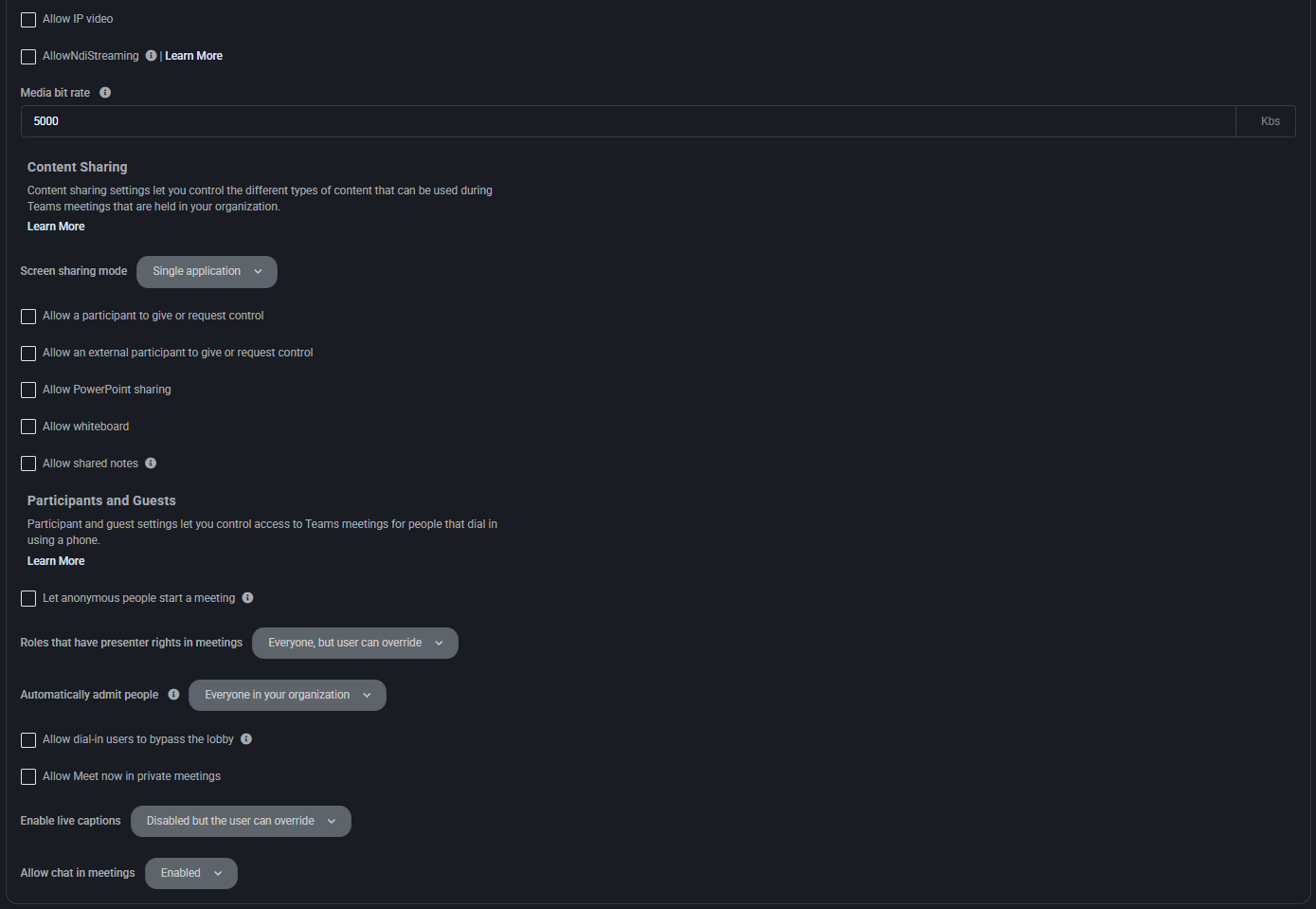
Messaging Policy
This section controls chat and messaging permissions for Teams users, including editing, deletion, media, and accessibility features.
- Use Org-wide Default policy: Inherits global messaging settings if enabled.
- Owners can delete sent messages: Allows team owners to delete any user message in a channel or chat.
- Delete sent messages: Enables users to delete their own sent messages.
- Edit sent messages: Enables users to modify their previously sent messages.
- Read receipts: Defines whether users can see if messages have been read; can be user-controlled or enforced.
- Chat: Toggles access to one-on-one and group chats in Teams.
- Use Giphys in conversations: Enables the use of GIFs via the Giphy integration in chat.
- Giphy content rating: Restricts Giphy content to Strict, Moderate, or Allow all content levels.
- Use Memes in conversations: Allows users to send memes via the built-in meme tool.
- Use Stickers in conversations: Enables sticker usage in chat messages.
- Allow URL previews: Displays clickable previews for links shared in chat.
- Translate messages: Allows users to translate messages into their preferred language.
- Allow immersive reader for viewing messages: Enables accessibility via Microsoft Immersive Reader.
- Send urgent messages using priority notifications: Lets users mark messages as urgent for repeated delivery alerts.
- Create voice messages: Allows users to send voice messages via Teams mobile or desktop client.
- On mobile devices, display favorite channels above recent chats: Prioritizes pinned channels over recent messages.
- Remove users from group chats: Enables the option to remove participants from ongoing group chats.
- Suggested replies: Displays AI-powered quick reply options below received messages.
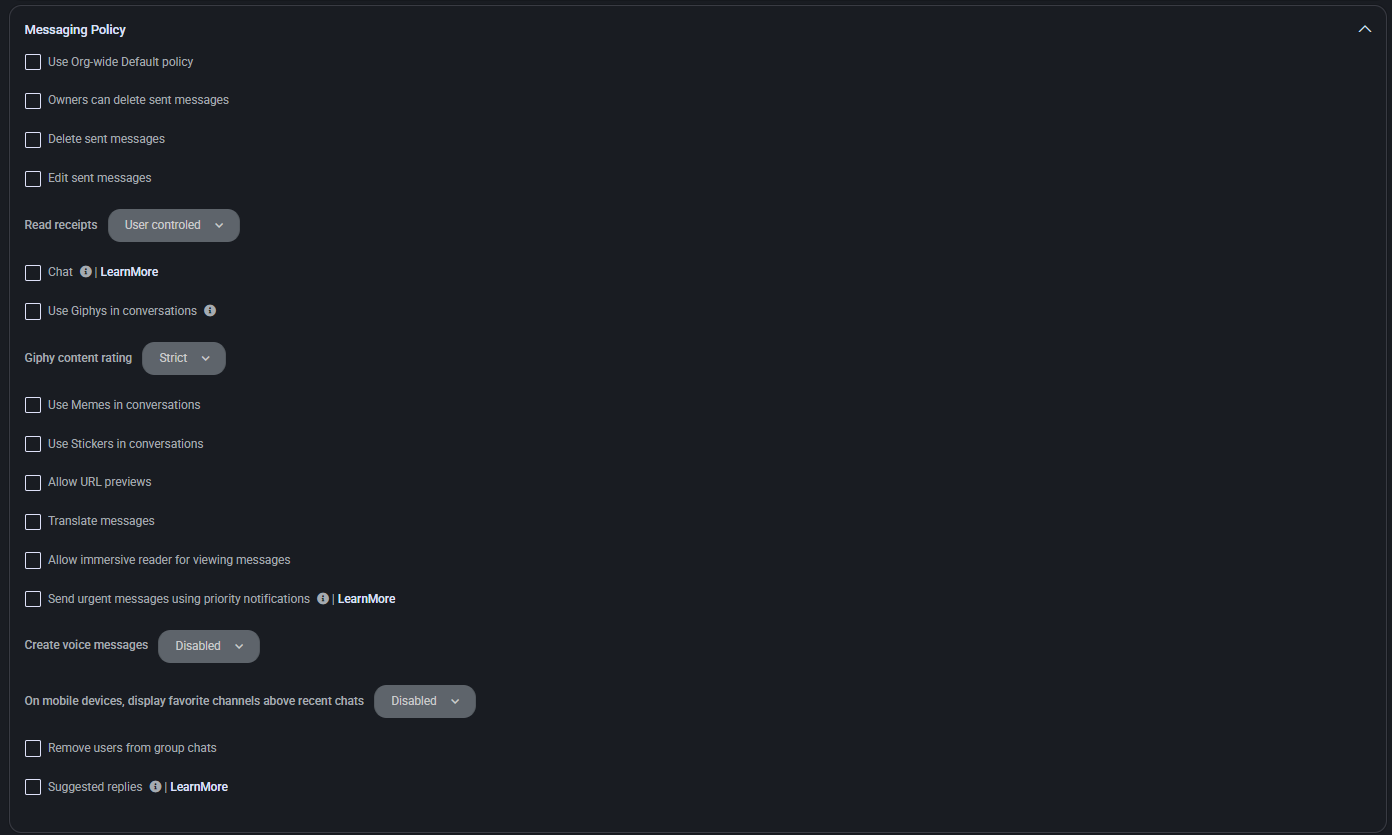
Live Events Policy
This section configures permissions and capabilities for hosting live events in Microsoft Teams.
- Use Org-wide Default policy: Inherits global live event policy settings if enabled.
- Allow scheduling: Grants users the ability to schedule live events within Teams.
- Allow transcription for attendees: Enables real-time transcription for participants viewing the live event.
- Who can join scheduled live events: Defines audience access level — options include:
- Everyone in the organization
- Specific users or groups
- Public (if allowed)
- Who can record an event: Determines whether recording is mandatory, optional, or disabled entirely. Options include:
- Always record
- Organizer only
- Never record
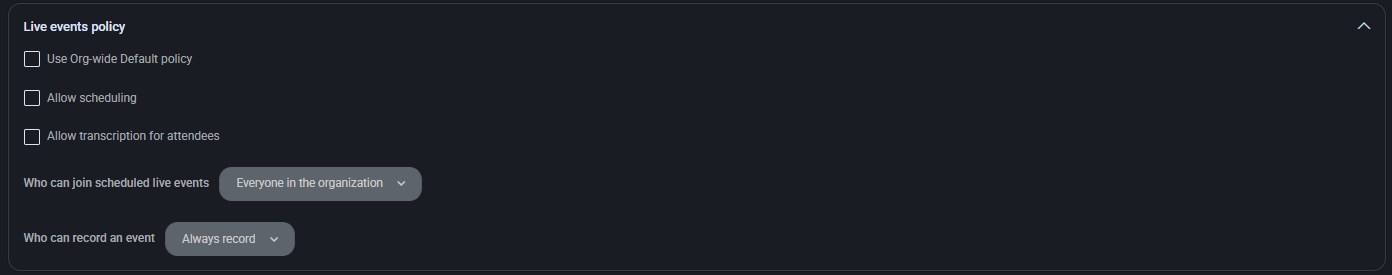
Call Park Policy
This section defines settings related to the call park feature, which allows users to place a call on hold and retrieve it from another device.
- Use Org-wide Default policy: Applies the organization-wide default call park policy to this user plan.
- Allow call park: Enables the ability to park calls and retrieve them using a pickup code.
Calling Policy
Configure calling behavior and access permissions for Teams voice capabilities.
- Use Org-wide Default policy: Inherit calling settings from the organization’s global policy.
- Make private calls: Allow users to make calls that do not appear in call history.
- Call forwarding and simultaneous ringing to people in your organization: Permit users to forward calls or ring additional internal contacts.
- Call forwarding and simultaneous ringing to external phone numbers: Permit call redirection to outside phone numbers.
- Voicemail is available for routing inbound calls: Toggle voicemail availability as a destination option for inbound call routing.
- Inbound calls can be routed to call groups: Allow routing of incoming calls to predefined groups of users.
- Allow delegation for inbound and outbound calls: Enable users to make and receive calls on behalf of others.
- Prevent toll bypass and send calls through the PSTN: Forces all outbound calls to go through PSTN, disallowing internal network bypass.
- Busy on busy is available when in a call: Configure if new incoming calls are rejected while the user is already in another call.
- Allow web PSTN calling: Enable PSTN calls directly from web-based Teams clients.
Caller ID Policy
This section manages the configuration of how caller identity is displayed when placing outbound calls through Teams.
- Use Org-wide Default policy: Applies the organization’s default caller ID settings to this user plan.
- Block incoming caller ID: Hides the caller ID on incoming calls to this user.
- Override the caller ID policy: Allows this plan to define a caller ID behavior different from the global setting.
- Replace the caller ID with: Choose whether to use a service number or another identity for outbound caller ID.
- Replace the caller ID with this service number: Specify the exact service number to show as the outbound caller ID.
Teams Policy
This section controls access to advanced Teams functionality, particularly private channel management.
- Use Org-wide Default policy: Inherits settings from the global Teams configuration.
- Create private channels: Allows users to create private channels within Teams, enabling segmented communication and restricted visibility.
Emergency Calling Policy
This section controls how users can access emergency calling features in Microsoft Teams. These policies allow administrators to configure notifications when emergency numbers are dialed and customize the scope of who receives these alerts.
- Use Org-wide Default policy: Inherits emergency call settings from the global default policy.
- Notification mode: Determines how the system handles emergency call alerts. Options include:
- Send notification only: Triggers alerts without routing the call directly.
- Numbers to dial for emergency calls notifications: Specifies which numbers will be alerted when an emergency number is dialed.
Note: If notification mode is set to Send notification only, a notification group must be configured to receive alerts.
Update Policy
This section allows administrators to configure Teams update delivery and visibility of new features for users assigned to the plan.
- Use Org-wide Default policy: Applies the general Teams update settings across the organization.
- Show preview features: Enables early access to Microsoft Teams features before they are officially released, useful for testing and internal evaluation.
Dial Plan
This section allows configuration of dial plans to normalize phone number formats into a standard (E.164) format used across the organization.
- Use Org-wide Default policy: Inherit settings from the organization’s global dial plan.
- Description: Free-text field for internal notes or plan identification.
Dial Plan Details
Specify how dialed numbers should be translated using normalization rules.
Normalization Rules
Defines rules for transforming input phone numbers into standard formats. These rules are applied in sequence from top to bottom. Each rule must be explicitly assigned to the dial plan.
Emergency Call Routing Policy
This section allows you to define how emergency calls are routed within the organization when using Direct Routing.
- Use Org-wide Default policy: Inherit emergency routing rules from global configuration.
- Description: Internal notes field for documentation or tracking purposes.
- Dynamic emergency calling: Enables dynamic location-based routing for emergency services.
Emergency Numbers
Defines emergency contact numbers like 911, 999, or 112. These can be routed differently for each region or policy.
Voice Routing Policy
This policy determines how outbound calls are routed through the PSTN based on rules and usage priorities.
- Use Org-wide Default policy: Inherit settings from the organization’s default voice routing policy.
- Description: Free-form field for providing context or purpose of the plan.
PSTN Usage Record
Lists usage patterns and rules for routing calls. Usage records are evaluated in order until a match is found and used to determine routing behavior.
Best Practices
- Use Org-wide Default policy settings only if consistent global rules apply — customize locally when needed for specific user groups.
- For dial plans, clearly document all normalization rules and test translations for common input formats to avoid call failures.
- Ensure emergency call routing policies comply with local regulations and include all relevant emergency numbers for each region.
- Regularly audit PSTN usage records to ensure efficient routing and avoid unnecessary toll charges or call routing loops.
- For voice routing policies, use descriptive labels and keep usage priorities clearly ordered to support easy troubleshooting and configuration scaling.
SharePoint Policy
The SharePoint Policy section defines rules for usernames, group names, password complexity, expiration periods, and end-user portal behavior. These policies help enforce consistency, security, and operational standards across your SharePoint environment.
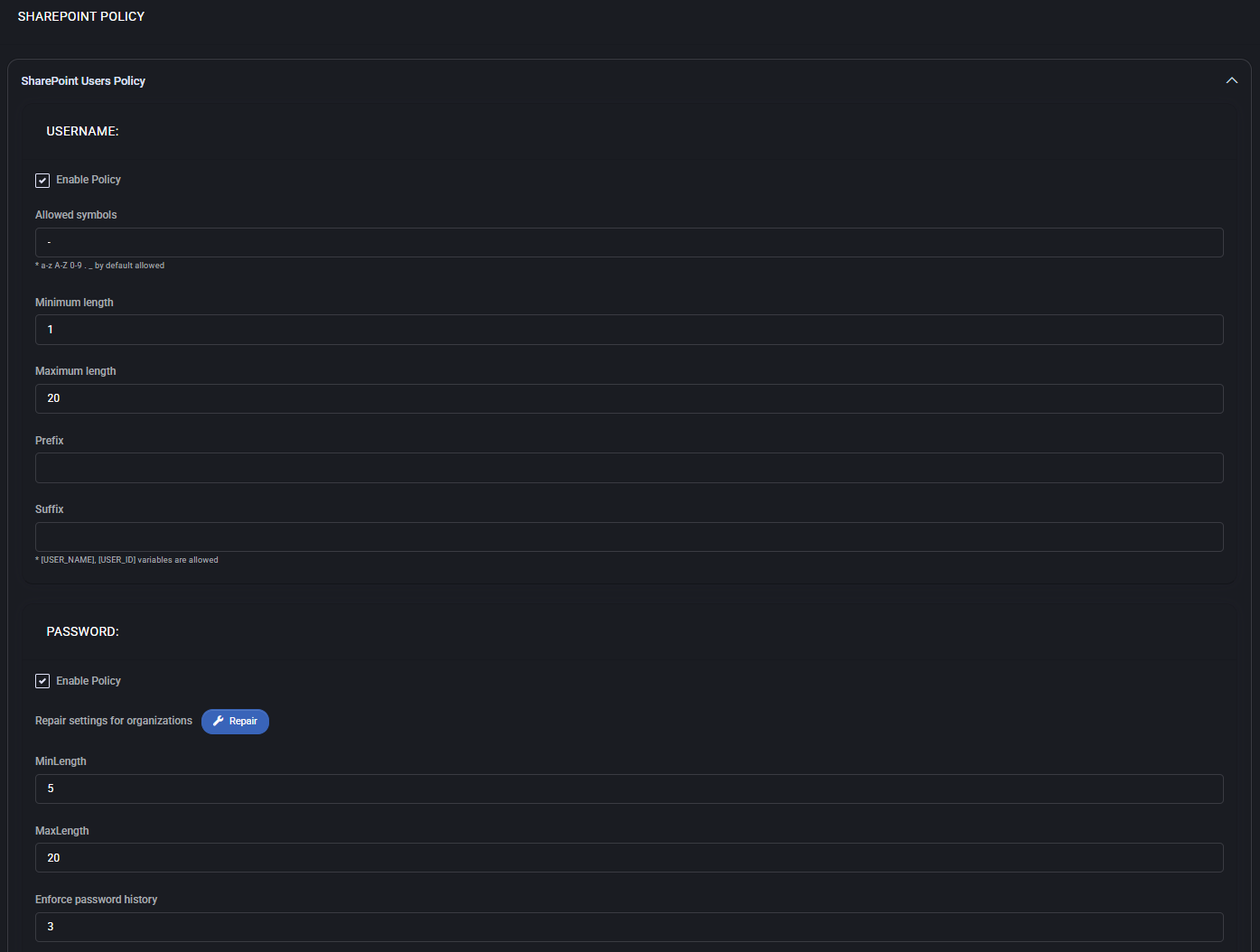
SharePoint Users Policy
This section allows you to define user-specific rules for SharePoint access.
Username
- Enable Policy: Activate custom username rules.
- Allowed symbols: Define acceptable characters; by default, a-z, A-Z, 0-9 are allowed.
- Minimum length: Set the shortest acceptable username length.
- Maximum length: Set the longest acceptable username length.
- Prefix: Optional static prefix for all usernames.
- Suffix: Optional static or dynamic suffix; variables such as
{USER_NAME} and {USER_ID} are supported.
Password
- Enable Policy: Enable or disable custom password policy.
- Repair settings for organizations: Reset non-compliant settings with one click.
- MinLength / MaxLength: Define minimum and maximum password lengths.
- Enforce password history: Number of unique passwords remembered before reuse is allowed.
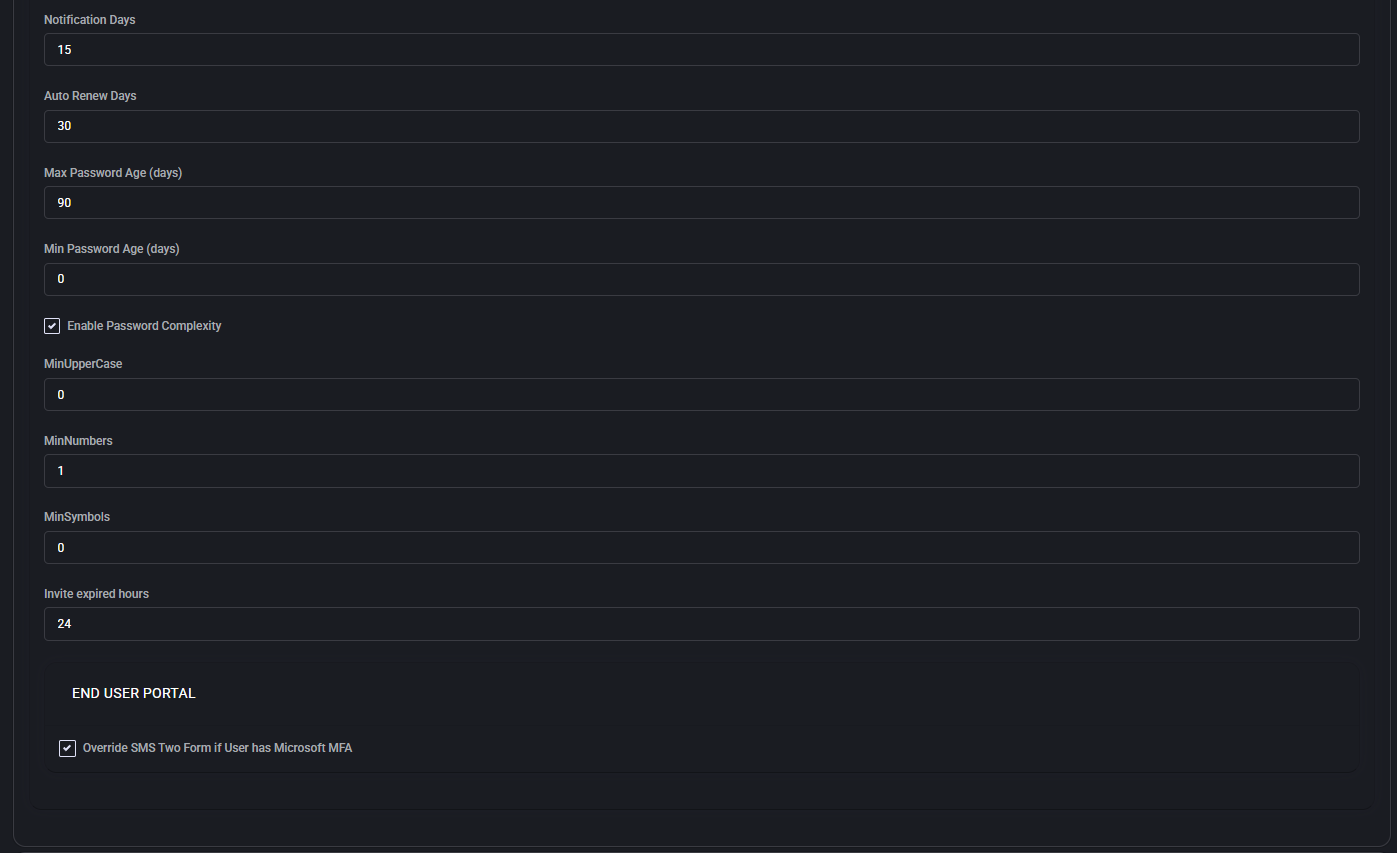
- Notification Days: When to notify users prior to password expiration.
- Auto Renew Days: Automatic renewal window before expiry.
- Max Password Age / Min Password Age: Define how long passwords remain valid or when they can be changed.
- Enable Password Complexity: Toggle complexity enforcement options.
- MinUpperCase / MinNumbers / MinSymbols: Set minimum character requirements for complexity.
- Invite expired hours: Time limit for invite link expiration.
End User Portal
- Override SMS Two Form if User has Microsoft MFA: Bypass internal 2FA if Microsoft MFA is already in place.
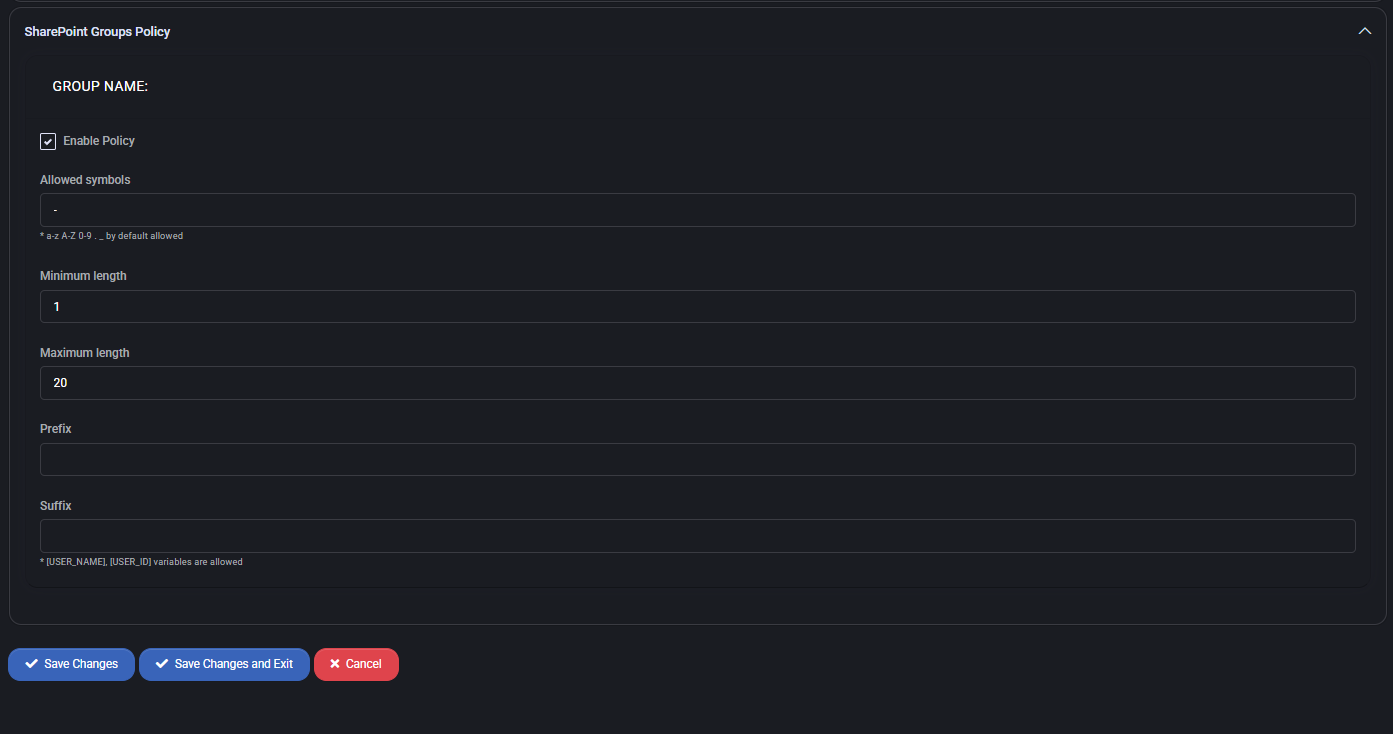
SharePoint Groups Policy
This section allows you to define naming rules for SharePoint groups, similar to user account naming policies.
- Enable Policy: Enforces the group naming rules defined below.
- Allowed symbols: Define special characters allowed in group names; a-z, A-Z, 0-9 are always allowed by default.
- Minimum length: Set the shortest acceptable group name.
- Maximum length: Set the maximum length of group names.
- Prefix: Optional static prefix for group names to enforce consistency.
- Suffix: Optional suffix; can include dynamic variables like
{USER_NAME} and {USER_ID}.
Best Practices
- Use consistent naming conventions for both users and groups to streamline management and automation workflows.
- Limit allowed symbols to ensure compatibility with downstream systems and integrations.
- Enable password complexity and set minimum requirements to meet common compliance frameworks.
- Use dynamic suffixes in usernames and group names when appropriate to guarantee uniqueness.
- Set realistic expiration periods and enable user notifications to avoid unexpected access lockouts.
- If using Microsoft MFA, enable the override option to simplify the authentication process for users.
Hosted Organization Policy
The Hosted Organization Policy section defines rules for user credentials, security, authentication, organization identifiers, archive settings, migration options, and related notifications. These policies enforce consistent behavior and compliance across all hosted organizations managed in MSPControl.
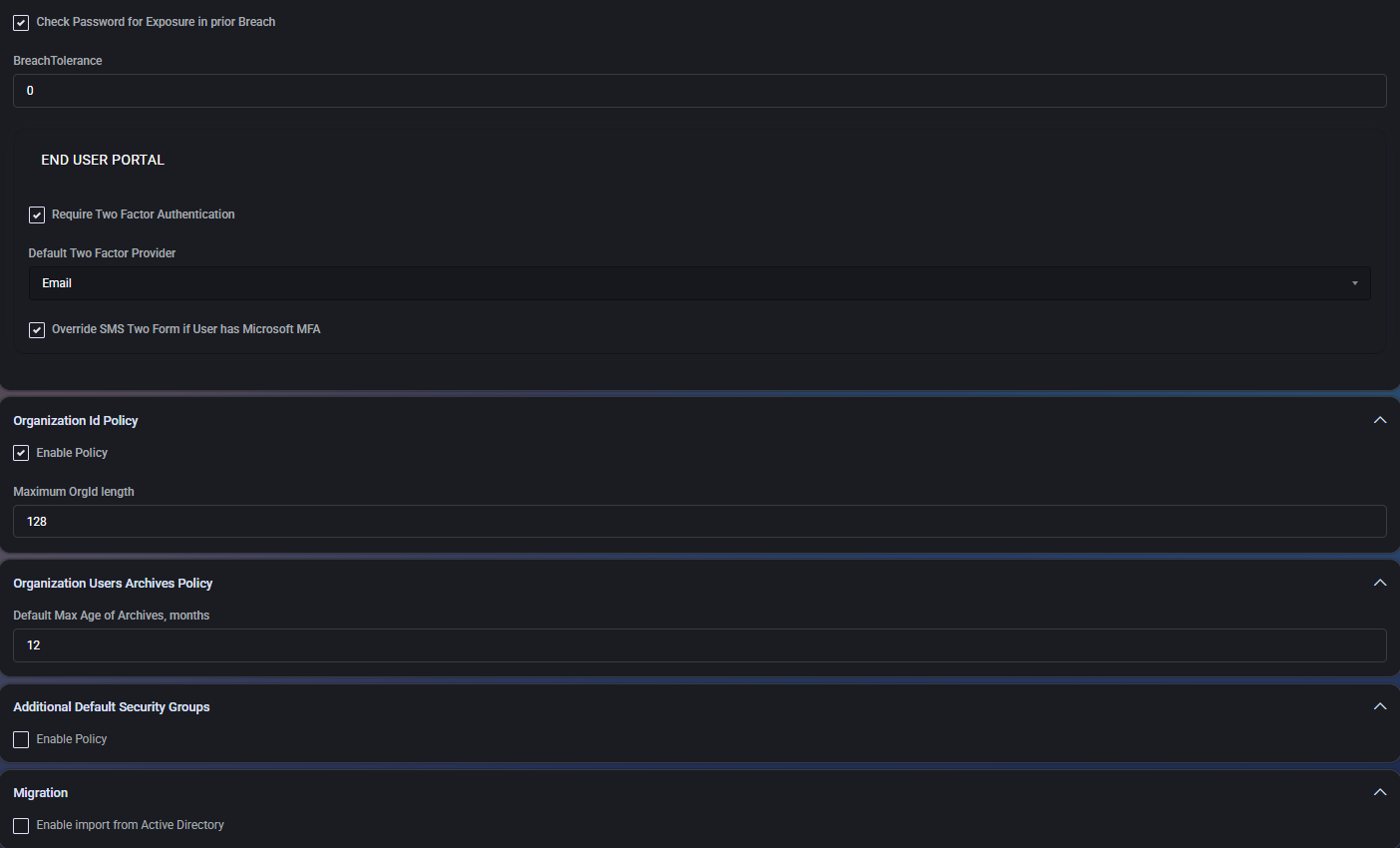
Check Password for Exposure in Prior Breach
Activates a check against known breach databases (such as HaveIBeenPwned) when new passwords are set. If the password has been previously exposed, the system can prompt users to select a more secure alternative.
- Breach Tolerance: Set to
0 by default, disallowing any exposed passwords.
End User Portal Settings
Controls how users authenticate and interact with the portal.
- Require Two Factor Authentication: Forces MFA for portal access.
- Default Two Factor Provider: Specifies the primary provider used (e.g., Email).
- Override SMS Two Form if User has Microsoft MFA: Prevents double-MFA scenarios if the user is already protected by Microsoft.
Organization ID Policy
Defines constraints for organization identifiers.
- Enable Policy: Enforces this policy when checked.
- Maximum OrgId Length: Sets a length limit (default:
128 characters).
Organization Users Archives Policy
Controls automatic archival of user accounts.
- Default Max Age of Archives: Defines maximum age in months before automatic archiving (default:
12).
Additional Default Security Groups
Optionally applies additional security groups to new users or organizations.
- Enable Policy: Enables this functionality.
Migration
Handles directory synchronization options.
- Enable import from Active Directory: Imports and manages users from on-premise AD infrastructure.
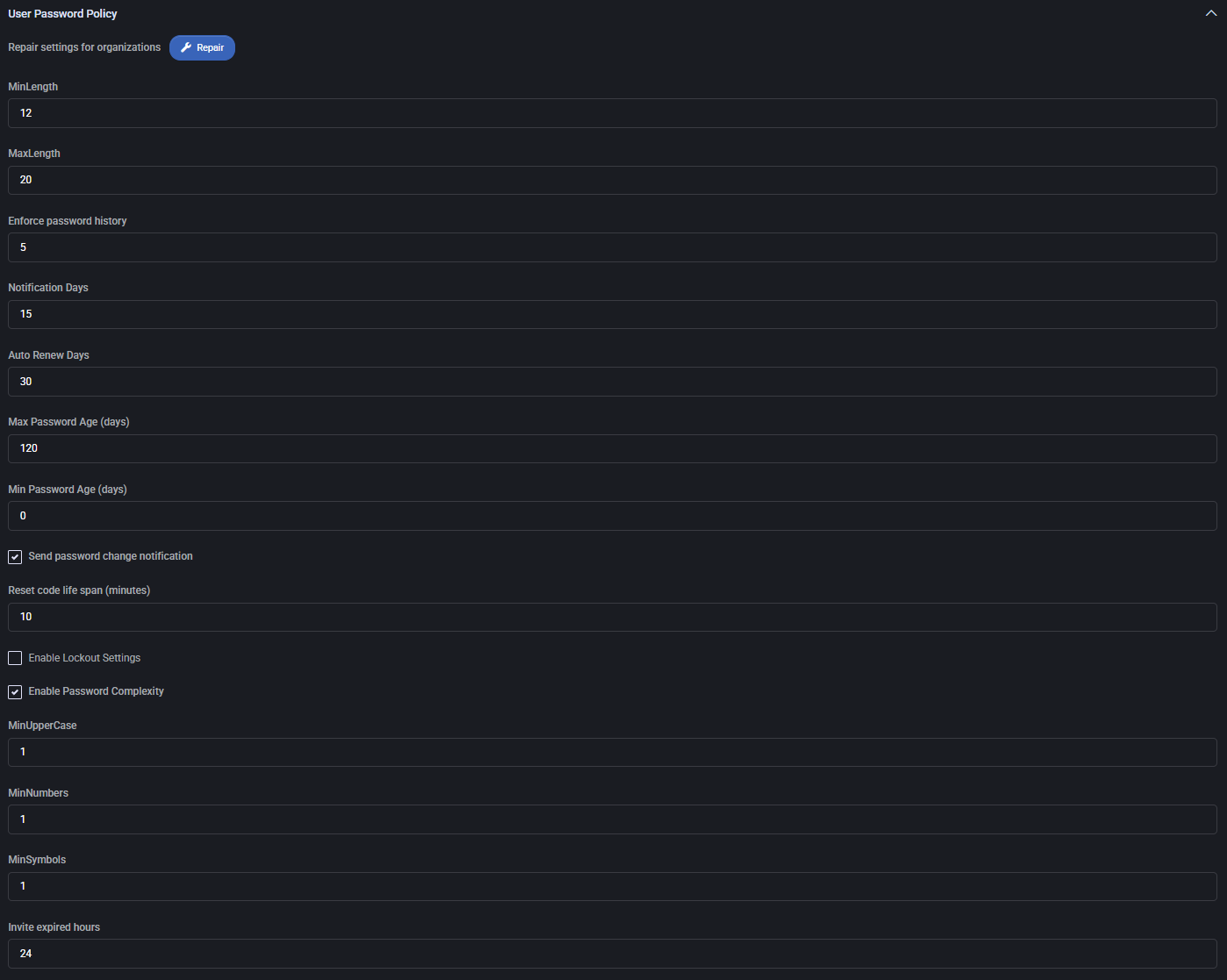
User Password Policy
Sets restrictions and behavior for user passwords within hosted organizations.
- Repair Settings: Resets organizational password policies to default values.
- MinLength: Minimum password length (default:
12).
- MaxLength: Maximum password length (default:
20).
- Enforce Password History: Prevents reusing recent passwords (default: last
5).
- Notification Days: Alerts users before expiration (default:
15 days).
- Auto Renew Days: Duration between automatic password resets (default:
30 days).
- Max Password Age: Expiration period in days (default:
120).
- Min Password Age: Prevents password change before defined days (default:
0).
- Send Password Change Notification: Enables email alert upon password change.
- Reset Code Life Span: Code validity period in minutes (default:
10).
- Enable Lockout Settings: Optional lockout for repeated failed logins.
- Enable Password Complexity: Enables enforcement of complex password rules.
- MinUpperCase / MinNumbers / MinSymbols: Require at least 1 uppercase, number, and symbol respectively.
- Invite Expired Hours: Invitation links are valid for
24 hours.
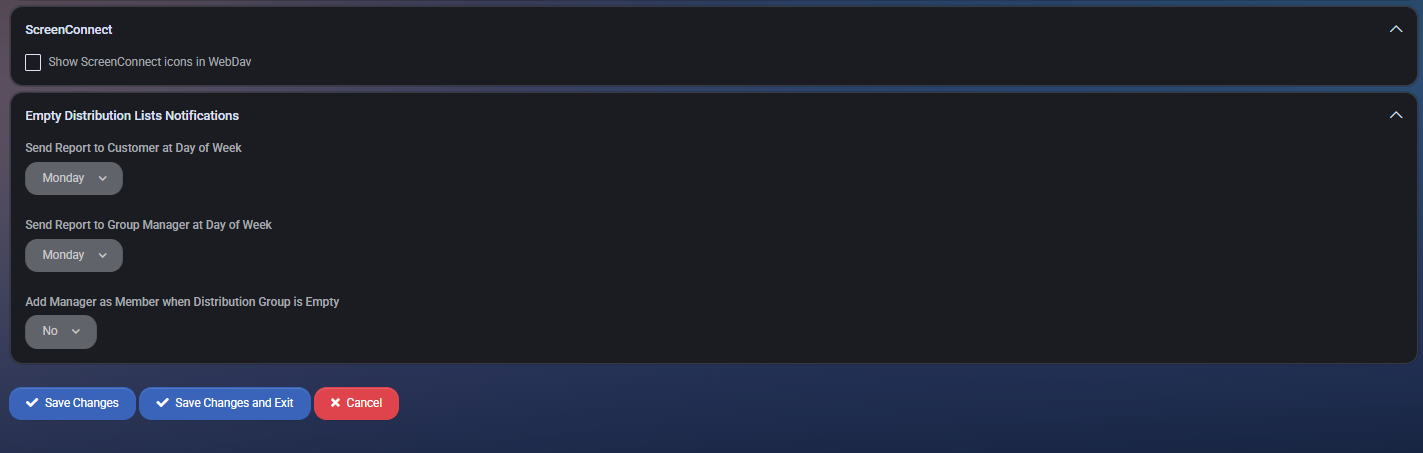
ScreenConnect
WebDAV integration for remote access.
- Show ScreenConnect icons in WebDav: If enabled, adds integration icons into user file managers.
Empty Distribution Lists Notifications
Sends alerts for unpopulated distribution groups.
- Send Report to Customer at Day of Week: Day to send automated empty-group report to customers.
- Send Report to Group Manager at Day of Week: Weekly report for group admins.
- Add Manager as Member when Distribution Group is Empty: Automatically assigns the manager as a fallback member if the group has no participants.
Best Practices
- Always enable breach detection for improved security hygiene.
- Define realistic password aging and complexity values that balance security with usability.
- Use 2FA (especially Microsoft MFA) as a default security baseline.
- Limit OrgId lengths if integrating with external systems to prevent overflows.
- Keep archive retention aligned with compliance or operational policies (e.g., 12 or 24 months).
- Enable automatic Active Directory import only in hybrid environments.
- Monitor empty distribution lists to ensure organizational mailing groups are functional and up-to-date.
Service Levels
The Service Levels section defines predefined tiers or categories of service applied to customers or users within the MSPControl system. These levels can reflect the scope of IT support provided, feature access, or billing structure. The section also includes optional integration with ConnectWise via contact type mapping.
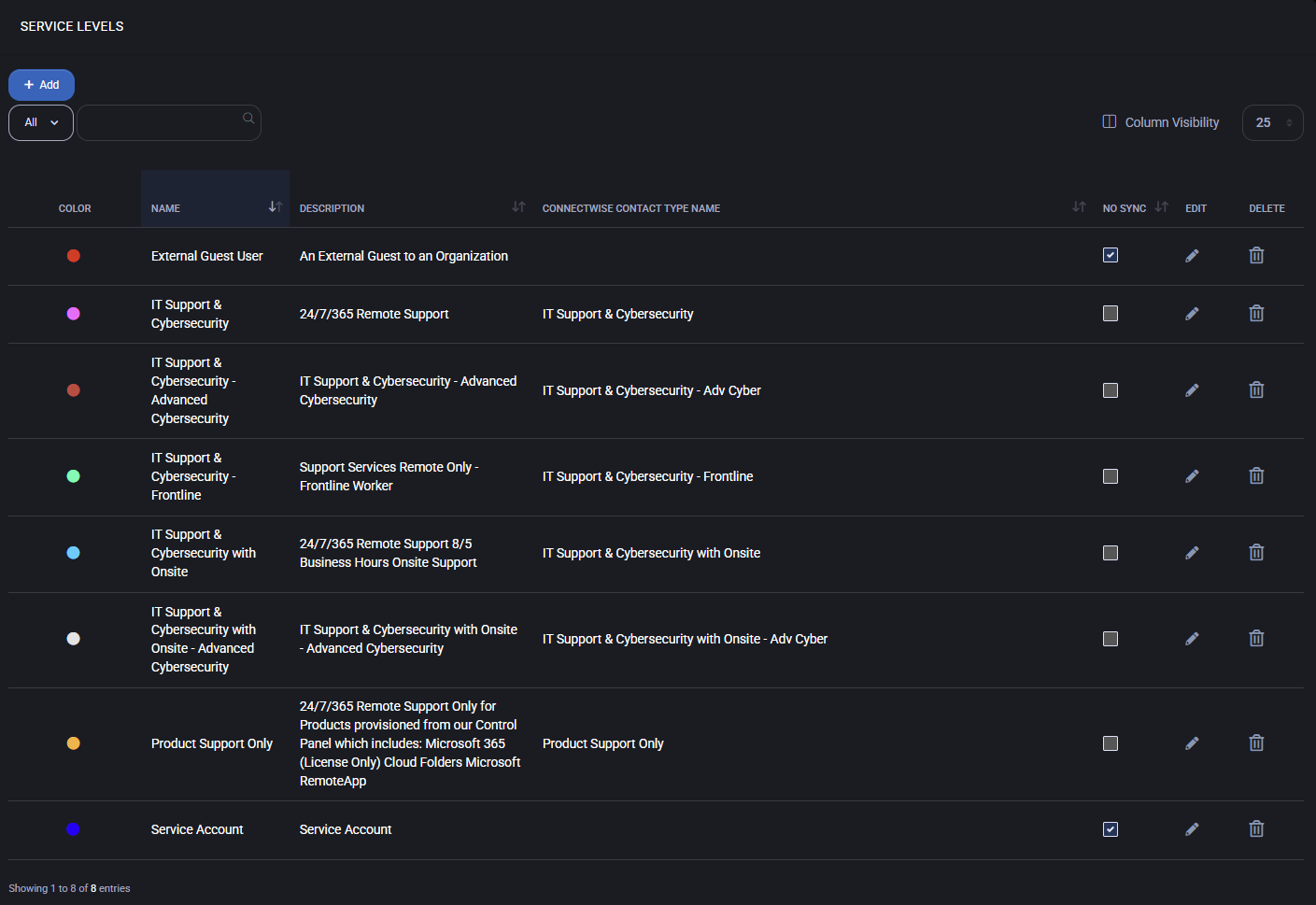
Service Level List
This table displays all existing service levels in the system:
- Name: Internal name of the service level (e.g., “External Guest User”, “IT Support & Cybersecurity”).
- Description: Free-text field describing what the level offers (e.g., “24/7/365 Remote Support”).
- Color: Each level can be visually tagged with a color for quick identification.
- ConnectWise Contact Type Name: Optional field for syncing this level with ConnectWise contact types.
- No Sync: When enabled, disables synchronization with external systems like ConnectWise for that level.
- Edit/Delete: Icons to modify or remove the corresponding service level.
You can sort the list by clicking on column headers (Name, Description, etc.) and control visible columns using the “Column Visibility” menu in the top right corner.
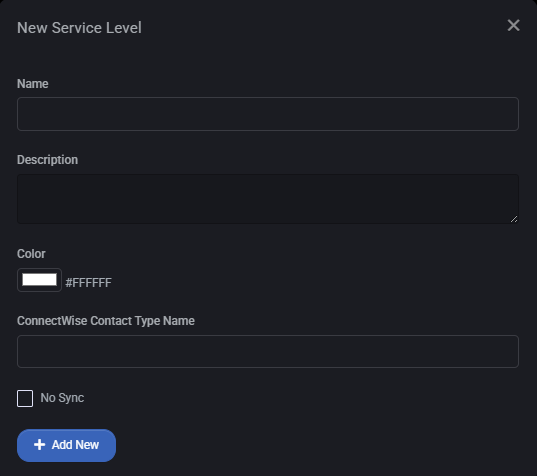
Add or Edit Service Level
Click + Add to create a new service level. The configuration panel includes the following fields:
- Name – The display name for the service level.
- Description – Description of what the level offers or represents.
- Color – Select a color code to visually represent this level in the UI.
- ConnectWise Contact Type Name – Optional mapping to a ConnectWise contact type.
- No Sync – Checkbox to prevent synchronization with external systems.
Click Add New to save the service level.
Best Practices
- Use color coding consistently to visually group similar service types.
- Clearly describe each level’s support scope (e.g., remote vs onsite, basic vs advanced cybersecurity).
- If using ConnectWise integration, ensure the contact type name matches the external system exactly.
- Use “No Sync” for levels that are internal only or not relevant for external ticketing/workflows.
Windows Agent Policy
This section allows administrators to configure custom policies for Windows agents deployed on end-user machines. Policies control update behavior, local settings, security hardening, and application management. Administrators can create, copy, or delete multiple profiles tailored to different device types such as servers or workstations.
Policy List
This table displays all existing Windows Agent Policies. Only the Default policy is included by default; the others (e.g., Server, Workstation, Workstation-Personal) were manually created as examples. Each policy shows its name, type, and available actions, such as duplicate, edit, or delete.
- Default – The only predefined configuration template available upon system installation
- Server – Example custom policy created for Windows Server environments
- Workstation – Example policy for general end-user machines
- Workstation-Personal – Example policy customized for personal-use endpoints
Use the Create button to define a new custom profile. Each profile can be uniquely configured using multiple setting tabs.
Device Profile
This section defines granular configuration options for Windows agents assigned to user devices. Settings are grouped by device-level behaviors and OS-related policies.
Settings
Automatically detect settings
Enables automatic configuration detection for managed devices.
Auto-Update Autopilot
Keeps Autopilot configuration updated automatically.
Drive Mapping
Controls user drive mapping policies on the device.
Federated Search
Allows federated search folders to be pushed to the system.
Low Space Alert
Triggers alerts when available disk space falls below the configured threshold.
Upload Max Size or Timeout
Limits the size and time for data uploads from the device.
Number of Days before Orphaned
Sets the number of days without agent check-in before the device is marked as orphaned.
RemoteApp Folder
Specifies the folder name used when assigning RemoteApps to the user.
Wsus Server
Defines the internal WSUS server URL for Windows Updates.
WSUS Target Group
Target group for WSUS updates.
WSUS Feature Update Group
Specifies OS versions for applying feature update policies (Windows 7–11, Server 2008–2022).
MAPI Profile
Allows configuration of local Outlook profile type (e.g., On-Premise or Cloud).
Trusted Sites
Manages browser or system-level trusted zones.
Warranty Info Enabled
Enables collection of warranty status and related metadata.
Geolocation
Allows geolocation data collection (may allow user override).
Telemetry Enabled
Enables system telemetry reporting for diagnostics and analytics.
Windows Update Settings
Applies Windows Update configuration through the agent.
Screen Saver
Enables enforcement of screen saver behavior.
Screen Saver – On resume, display logon screen
Forces password entry after resuming from screen saver.
Screen Saver Time Out, minutes
Specifies idle time (in minutes) before screen saver activates.
Sleep Timeout, when plugged in (seconds)
Inactivity threshold before sleep mode triggers on AC power.
Sleep Timeout, on battery power (seconds)
Sleep timeout while on battery power.
Display Timeout, when plugged in (seconds)
Turns off display after inactivity on plugged-in devices.
Display Timeout, on battery power (seconds)
Controls screen timeout duration while on battery.
Intune Device Ownership Enabled
Marks the device as company-owned within Microsoft Intune.
Auto-Enroll in Intune if member of Azure AD
Automatically enrolls device in Intune if joined to Azure AD.
Microsoft Defender
Ensures Microsoft Defender is enabled on the system.
Device Local Admin Enabled
Grants the user local administrator rights on the device.
Windows Disk Cleanup
Runs disk cleanup utilities automatically.
Third Party Patching
Allows patch management for third-party (non-Microsoft) applications.
Enroll in Microsoft Autopilot
Registers the device with Microsoft Autopilot for provisioning.
Max Upload Size, MB
Specifies maximum upload file size from the device.
Max Upload Timeout, seconds
Sets the timeout limit for uploads from the agent.
Low Space Alert, GB
Defines the free space limit to trigger low space alert (in GB).
RemoteApp Folder Name
Custom folder label under which RemoteApps appear.
Federated Search Folder Name
Custom name for federated search folders applied by the policy.
OS for Feature Update Group
Selects OS versions targeted by WSUS feature updates.
Screen Saver (dropdown)
Provides a list of selectable screen saver types.
Sleep Timeout (seconds)
Sleep timer for devices without separation by power source.
Never
Disables sleep timeout if checked.
Sleep Timeout, on battery power (seconds)
Defines the idle time before the system enters sleep mode on battery power.
Display Timeout, when plugged in (seconds)
Specifies how long the screen remains on while the system is plugged in.
Display Timeout, on battery power (seconds)
Specifies how long the screen remains on while running on battery power.
Azure IoT Hub connection string
Field for providing the Azure IoT Hub connection string, if used for device management.
Telemetry Storage Connection String
Used to store telemetry data collected from managed devices.
Telemetry Storage Container
Specifies the name of the Azure Blob container used to store telemetry data.
Azure Maps Account API Key
API key for integrating with Azure Maps location services.
Device Profile: Warranty Info
HP API URL
URL for querying HP device warranty data.
HP API Key
Authentication key for accessing HP warranty API services.
HP API Secret
Secret token used for secure access to HP warranty API.
Device Profile: Windows Update Settings
Auto Update Enabled
Controls whether automatic updates are enabled for the device.
Auto Update Options
Defines the update behavior, such as download and install scheduling.
Scheduled Install Day / Time
Specifies when updates should be installed (day and time).
Auto Reboot With Logged On Users
Determines if the system is allowed to reboot while users are logged in.
Always automatically restart at the scheduled time / timeout
Forces device restart after a specific timeout when scheduled installs occur.
Include Recommended Updates
If enabled, recommended updates will be installed in addition to critical ones.
Install updates for other Microsoft products
Expands updates to include non-Windows Microsoft software.
Show a notification when restart is needed
Displays a prompt when a restart is required after update.
Notification dismissal method
Sets how update notifications are dismissed (e.g., manually or auto).
Enable Active Hours
Activates protection against restarts during user-defined hours.
Active Hours Start / End
Defines the window during which restarts are restricted.
SLA for Number of Days
Service Level Agreement expectation for completing updates.
Check OS Version for Servicing Support
Verifies if the OS version is eligible for updates.
Use Update Class Policy Source
Determines whether to inherit update class settings from policy source.
Set Policy Driven Update Source for:
Provides granular control over update sources for:
- Feature Updates
- Quality Updates
- Driver Updates
- Other Updates
Third Party Patching
Configure automated patching of non-Microsoft (third-party) applications.
This section allows administrators to schedule recurring tasks to apply patches across supported third-party software.
Fields include:
- AutoRun – Enables or disables the entire patching task.
- Run Task – Defines execution frequency (e.g., Weekly).
- Day of Week – Select the specific weekday to run the task.
- Start Time – Defines the time of day when patching begins.
- Auto Reboot With Logged On Users – If enabled, the system will automatically reboot even if users are logged in.
- Show a notification when your PC requires a restart – Notifies end users about required reboots after patching.
- Run updates under user context – Executes patching with the logged-in user’s credentials.
- Only when user is local Administrator – Limits patching execution to devices where the user has local admin rights.
Intune
Determines how the device is managed within Microsoft Intune.
The only available setting here is:
- Device Ownership – Select between Corporate or Personal to define how the device should be enrolled in Intune.
Windows Disk Cleanup
Enables automated cleanup of system files and temporary data to reduce storage usage and improve performance.
You can control the execution schedule and the specific file types that should be purged during cleanup.
Available fields:
- AutoRun – Enables or disables the cleanup task entirely.
- Run Task – Defines the cleanup frequency (e.g., Weekly).
- Day of Week – Selects which day the cleanup should run.
- Start Time – Specifies the exact time for execution.
Checkboxes allow granular control over the types of data to remove:
- Temporary Setup Files – Removes files created during Windows setup.
- Old Chkdsk Files – Deletes log files from past Check Disk scans.
- Setup Log Files – Clears installation logs created by Windows or third-party software.
- Microsoft Defender Antivirus – Cleans up AV scan history and outdated definition logs.
- Diagnostic Data Viewer Database Files – Deletes system diagnostic history.
- Downloaded Program Files – Removes ActiveX controls and Java applets.
- Temporary Internet Files – Clears web browser caches (IE/Edge legacy).
- System Error Memory Dump Files – Deletes memory dumps generated after system crashes.
- System Error Minidump Files – Clears smaller crash dumps.
- Windows Error Reports and Feedback Diagnostics – Deletes reports generated by Windows Error Reporting (WER).
- Branch Cache – Removes cached content for branch office optimization.
- DirectX Shader Cache – Clears files created by the GPU shader compiler.
- Delivery Optimization Files – Deletes files used in peer-to-peer update delivery.
- Language Resources Files – Removes unused language packs.
- Recycle Bin – Empties the system recycle bin.
- Retail Demo Offline Content – Deletes demo materials for retail display devices.
- Temporary Files – Clears generic temporary files from the system.
- Thumbnails – Deletes image thumbnail cache files.
- User File History – Removes historical backups of user files.
- Catalog Files for the Content Indexer – Deletes indexing-related files.
- Downloads (Personal downloads folder) – Clears files from the user’s Downloads folder.
- Offline Files – Deletes cached files used for offline access.
- Windows Upgrade Log Files – Removes logs from previous Windows version upgrades.
- Windows Update Cleanup – Deletes outdated updates and update cache data.
Device Local Admin
Allows automated management of a predefined local administrator account on the endpoint.
This can be used for consistent access across devices, especially in environments where users are not local admins.
- Device Local Admin – Enables or disables creation of the account.
- Local Admin Username – Defines the username to be created (e.g.,
virtualadmin).
- Auto-Rotate Local Admin Password – When enabled, the password is automatically rotated at a set interval.
- Interval to Auto-Rotate (Days) – Sets the rotation frequency (e.g., every 90 days).
Security Hardening
The Security Hardening section provides a list of configurable system policies focused on enhancing endpoint security. Each rule modifies OS, network, or application behavior to reduce vulnerabilities. The table includes columns for property name, affected system component, change type, and toggles for enabling the rule and allowing user control.
Enable ‘Local Security Authority (LSA) protection’
Secures the Local Security Authority process by preventing unsigned drivers and plug-ins from being loaded. Enhances credential protection on Windows systems.
Set User Account Control (UAC) to automatically deny elevation requests
Prevents unauthorized applications or users from attempting privilege elevation by default denial.
Enable ‘Require additional authentication at startup’
Forces multi-factor or secure boot mechanisms to be enforced at system startup.
Set default behavior for ‘AutoRun’ to ‘Enabled: Do not execute any autorun commands’
Disables execution of autorun.inf files to prevent malware propagation through removable media.
Set LAN Manager authentication level to ‘Send NTLMv2 response only. Refuse LM & NTLM’
Improves authentication protocol security by eliminating older, less secure LM and NTLM methods.
Disable Anonymous enumeration of shares
Prevents unauthenticated users from discovering shared folders on the system.
Disable ‘Installation and configuration of Network Bridge on your DNS domain network’
Blocks creation of network bridges which could be used to bypass network segmentation policies.
Enable Local Admin password management
Allows centralized and secure rotation or assignment of local administrator passwords.
Disable the local storage of passwords and credentials
Prevents Windows from saving passwords in local stores, reducing credential theft risks.
Enable ‘Microsoft network client: Digitally sign communications (always)’
Requires SMB packets to be signed, ensuring data integrity and helping prevent man-in-the-middle attacks.
Enable ‘Apply UAC restrictions to local accounts on network logons’
Limits local accounts’ ability to perform elevated operations over network sessions, improving remote access security.
Prohibit use of Internet Connection Sharing on your DNS domain network
Disables ICS to prevent endpoints from acting as unauthorized internet gateways.
Disable running or installing downloaded software with invalid signature
Blocks untrusted software lacking a valid digital signature from execution or installation.
Disable ‘Continue running background apps when Google Chrome is closed’
Prevents Google Chrome from maintaining active processes after the browser window is closed, reducing background resource usage and potential vulnerabilities.
Disable ‘Password Manager’ in Google Chrome
Disables Chrome’s built-in password manager, encouraging use of more secure enterprise credential stores.
Disable ‘Always install with elevated privileges’
Prevents software installations from automatically using elevated privileges, reducing the attack surface during application deployment.
Disable JavaScript on Adobe DC
Disables JavaScript execution within Adobe Acrobat to reduce exposure to document-based exploits.
Enable ‘Require domain users to elevate when setting a network’s location’
Requires administrator approval for domain users when attempting to change network location, reducing misclassification of network zones.
Enable ‘Block third party cookies’ in Google Chrome
Prevents websites from saving third-party cookies, enhancing user privacy and reducing cross-site tracking.
Set controlled folder access to enabled or audit mode
Activates Microsoft Defender Exploit Guard’s Controlled Folder Access to restrict untrusted apps from making changes to protected directories.
Disable Flash on Adobe Reader DC
Removes support for Flash content in Adobe Reader DC, addressing known security vulnerabilities.
Disable JavaScript on Adobe Reader DC
Disables JavaScript execution in Adobe Reader to minimize risk from malicious scripts embedded in PDF files.
Set ‘Remote Desktop security level’ to ‘TLS’
Ensures Remote Desktop sessions use TLS for secure encrypted communications.
Enable ‘Limit local account use of blank passwords to console logon only’
Restricts blank password usage to local console access, blocking remote login attempts without proper credentials.
Disable ‘Device Install Software Request Error Report’ option
Turns off error reporting prompts related to device driver installation issues.
Prevent Internet Control Message Protocol (ICMP) redirects from overriding
Stops devices from accepting ICMP redirect packets, defending against certain network-level attacks.
Block outdated ActiveX controls for Internet Explorer
Prevents the execution of unsupported or outdated ActiveX components, mitigating legacy vulnerabilities in Internet Explorer.
Disable ‘Allow Basic authentication’ for WinRM Client
Disables legacy authentication for Windows Remote Management client to enforce stronger methods like Kerberos or certificate-based login.
Disable ‘Allow Basic authentication’ for WinRM Service
Same as above but applied to the server side (WinRM service), further securing remote management protocols.
Disable ‘Autoplay’ for non-volume devices
Blocks autoplay functionality for devices such as memory cards or digital cameras to prevent unwanted script execution.
Disable ‘Autoplay’ for all drives
Globally disables autoplay across all connected drives to mitigate autorun-based threats.
Disable ‘Enumerate administrator accounts on elevation’
Prevents Windows from listing available administrator accounts when elevation is required, reducing information leakage.
Disable IP source routing
Blocks IP packets that specify source routing, a rarely used option that can be abused to bypass network security policies.
Disable merging of local Microsoft Defender Firewall rules with group policy firewall rules for the Public profile
Ensures that only centrally managed Group Policy firewall rules are applied to the Public profile, overriding any local rules that may weaken security.
Disable merging of local Microsoft Defender Firewall connection rules with group policy firewall rules for the Public profile
Similar to the previous setting, this blocks local connection rules from merging with Group Policy settings for the Public profile.
Disable SMBv1 client driver
Disables the legacy SMBv1 protocol driver to reduce vulnerabilities from outdated network file sharing protocols.
Disable Solicited Remote Assistance
Blocks users from sending invitations for remote assistance, helping prevent unauthorized remote access attempts.
Hide Option to Enable or Disable Updates
Removes the UI options that allow users to enable or disable Windows Updates manually, helping enforce centralized update policies.
Microsoft Office Enable Automatic Updates
Enables automatic updates for Microsoft Office, ensuring the suite stays up to date with security patches and improvements.
Set IPv6 source routing to highest protection
Configures IPv6 to reject source routing headers, which can be used to bypass normal routing and launch network attacks.
Trusted Sites
This tab allows you to configure authentication behavior for different browser zones and manage a list of explicitly trusted URLs.
Internet Zone Settings
Logon (Intranet Zone)
Specifies how user authentication is handled for resources within the corporate intranet zone.
Logon (Trusted Zone)
Defines the authentication method for trusted sites explicitly added to the Trusted Sites list.
Logon (Internet Zone)
Determines the login behavior for general internet sites that don’t fall under other zones.
Logon (Restricted Zone)
Sets the login method for high-risk or limited-access sites in the restricted zone.
Each dropdown provides the following options:
- Do not change – Keeps the existing setting unchanged
- Automatic logon with current user name and password – Logs in automatically using the current Windows session credentials
- Prompt for user name and password – Requires manual entry of credentials on each access
- Automatic logon only in intranet zone – Enables automatic login only when accessing intranet resources
- Anonymous logon – Connects without providing any user credentials
Trusted Site
This section allows you to define a list of trusted URLs and assign them to specific zones. Trusted sites are typically internal company resources that require secure but streamlined authentication.
Each trusted site entry contains:
- Trusted Site – The base URL (e.g.,
https://cluster.example.local)
- Comments – Optional notes or description for the resource (e.g., “Virtuworks RDS Cluster”)
- Zone – Defines which zone the site is assigned to (e.g., Intranet, Trusted, Internet)
You can add a new site by entering the URL, an optional comment, selecting a zone from the dropdown, and clicking Add. To modify an existing record, click Edit, make your changes, and click Update.
Managed Applications
This tab defines which software applications should be automatically installed and managed on target devices during policy enforcement. Each application in the list includes two toggles:
- Enabled – If selected, the system will automatically deploy the application to the device.
- Allow User Control – If enabled, end-users will have the ability to modify the application state (e.g., uninstall).
The following managed applications are available:
- Install Azure Monitor – Enables remote monitoring of system performance and health via Azure Monitor.
- Install ScreenConnect Agent – Installs the remote access tool for IT support and administration.
- Install Microsoft Office 365 Apps – Installs the Microsoft 365 suite (Word, Excel, Outlook, etc.).
- Install TerminalWorks TSPrint Client – Adds virtual printing support for remote desktop sessions.
- Install TerminalWorks TSScan Client – Enables remote desktop scanning capabilities.
- Install Purview Information Protection – Deploys Microsoft Purview client for data classification and compliance.
- Install Microsoft Teams Client – Installs Microsoft Teams for collaboration and communication.
- Install Google Chrome – Installs the Chrome browser.
- Install Acrobat Reader DC – Adds the PDF reader from Adobe.
- Install Mimecast Plugin for Outlook – Installs email security and archiving features via Mimecast.
- Install Phish Alert Outlook Plugin – Adds anti-phishing reporting tools to Outlook.
Best Practices
- Use a descriptive name for each policy that reflects its intended purpose or target device group (e.g., Remote Workstations – Hardened).
- Start with the Device Profile tab to set foundational configurations such as disk cleanup and telemetry options.
- Enable only the Security Hardening policies that match your organization’s risk tolerance and security baseline. Not all systems require maximum lockdown.
- Review each Trusted Site and zone setting to ensure only internal, secure resources are whitelisted.
- In the Managed Applications tab, install only the software essential for productivity and security to minimize system bloat.
- Enable Allow User Control cautiously — only for applications or settings where user intervention is safe and supported.
- Test each policy in a staging environment before deploying it across production devices.
Veeam Backup Report Policy
This policy monitors the status and reliability of Veeam backups across managed endpoints. It is primarily used to generate compliance reports and detect backup issues before they become critical.
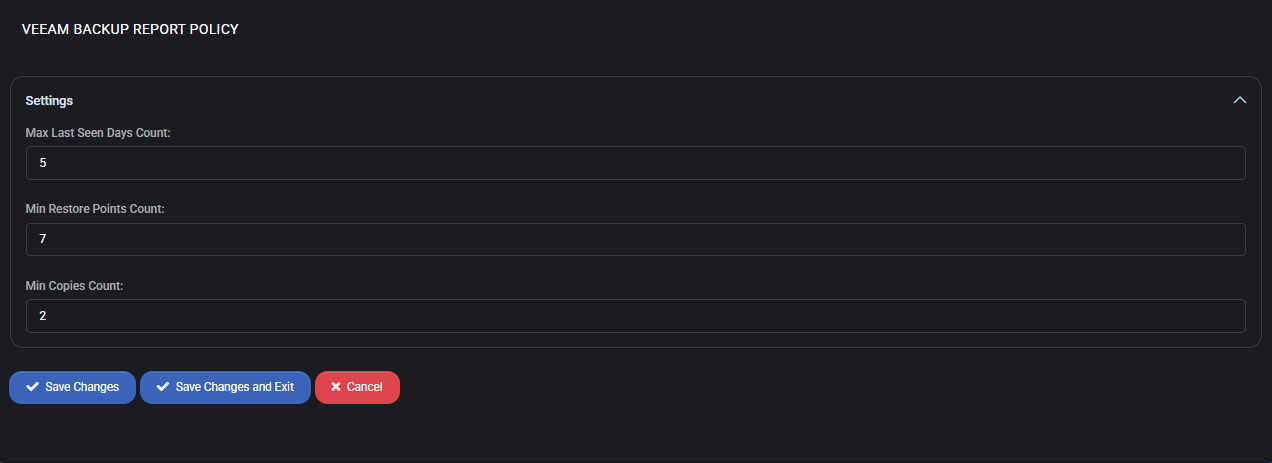
Settings
- Max Last Seen Days Count
Defines the maximum number of days a backup job can remain unseen in the system before it is flagged as inactive or missing.
For example, if a backup job has not been detected within 5 days, it will be considered non-compliant.
- Min Restore Points Count
Sets the minimum number of restore points required for each backup job to be considered valid.
A value of 7 ensures that there is at least one restore point per day over the course of a typical week.
- Min Copies Count
Indicates the minimum number of copies that must exist for a backup to meet redundancy and resilience standards.
With a setting of 2, this enforces a backup replication or offsite copy policy.
Best Practices
- Adjust Max Last Seen Days to reflect your organization’s expected backup frequency (e.g., daily or weekly).
- Ensure Min Restore Points aligns with your retention policy and recovery time objectives.
- Use Min Copies to enforce 3-2-1 backup strategies (3 total copies, 2 different media, 1 offsite).
- Pair this policy with alerting tools to notify administrators of non-compliant endpoints.
- Review backup compliance reports regularly to detect configuration drift or missed schedules.
Azure Backup Report Policy
This policy is used to monitor the integrity, availability, and compliance of Azure-based backup jobs across endpoints. It is especially useful for ensuring that restore points, retention periods, and visibility of backups meet defined standards for both cloud and on-premise environments.
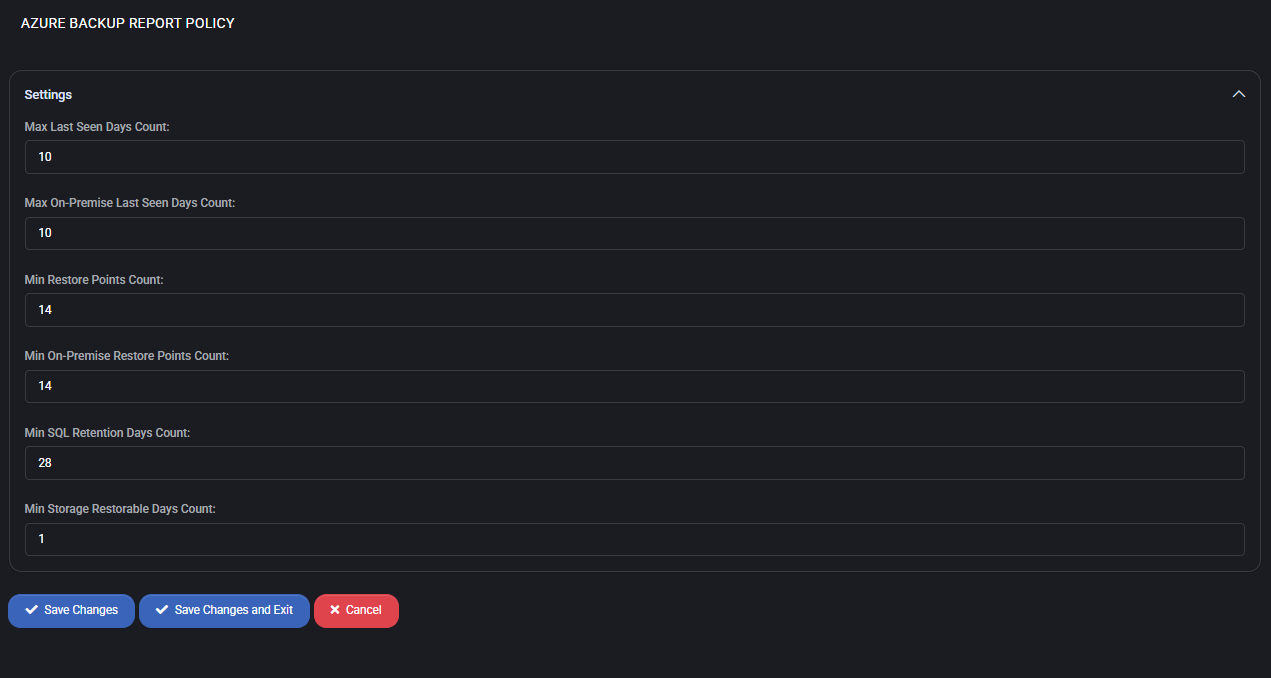
Settings
- Max Last Seen Days Count
The maximum number of days since a backup job was last seen. If no backup is detected within 10 days, it is flagged as non-compliant.
- Max On-Premise Last Seen Days Count
Same as above but applied specifically to on-premise endpoints. Ensures hybrid environments are also monitored for backup visibility.
- Min Restore Points Count
Sets the minimum number of restore points required for cloud-based backups to be considered valid. A value of 14 means two weeks of daily restore points must exist.
- Min On-Premise Restore Points Count
Defines the minimum required restore points for on-premise backup systems. Like the cloud value, it is set to 14 to reflect two weeks of coverage.
- Min SQL Retention Days Count
Minimum retention duration (in days) for SQL Server backups. A setting of 28 ensures backup data is available for four weeks before expiration.
- Min Storage Restorable Days Count
Sets the minimum number of days that deleted storage items (like disks or snapshots) should remain recoverable. Value 1 ensures at least one day of storage-level recoverability.
Best Practices
- Align Max Last Seen Days and Max On-Premise Last Seen Days with your monitoring intervals and SLA thresholds.
- Ensure that Min Restore Points reflect your recovery plan and legal compliance requirements (e.g., 7-day or 14-day recovery windows).
- Set Min SQL Retention conservatively for databases with longer retention needs or compliance mandates.
- Use Min Storage Restorable Days to prevent accidental permanent data loss when disks or volumes are deleted.
- Regularly audit this policy in combination with alerting systems to catch missed backups early.
Security Compliance Policy
The Security Compliance Policy allows you to define thresholds and enforcement rules for detecting misconfigurations, legacy practices, and other non-compliant behaviors in customer environments. This policy is split into three functional areas:
- Security Compliance Settings
- Baseline Policy Settings
- Azure MFA Settings
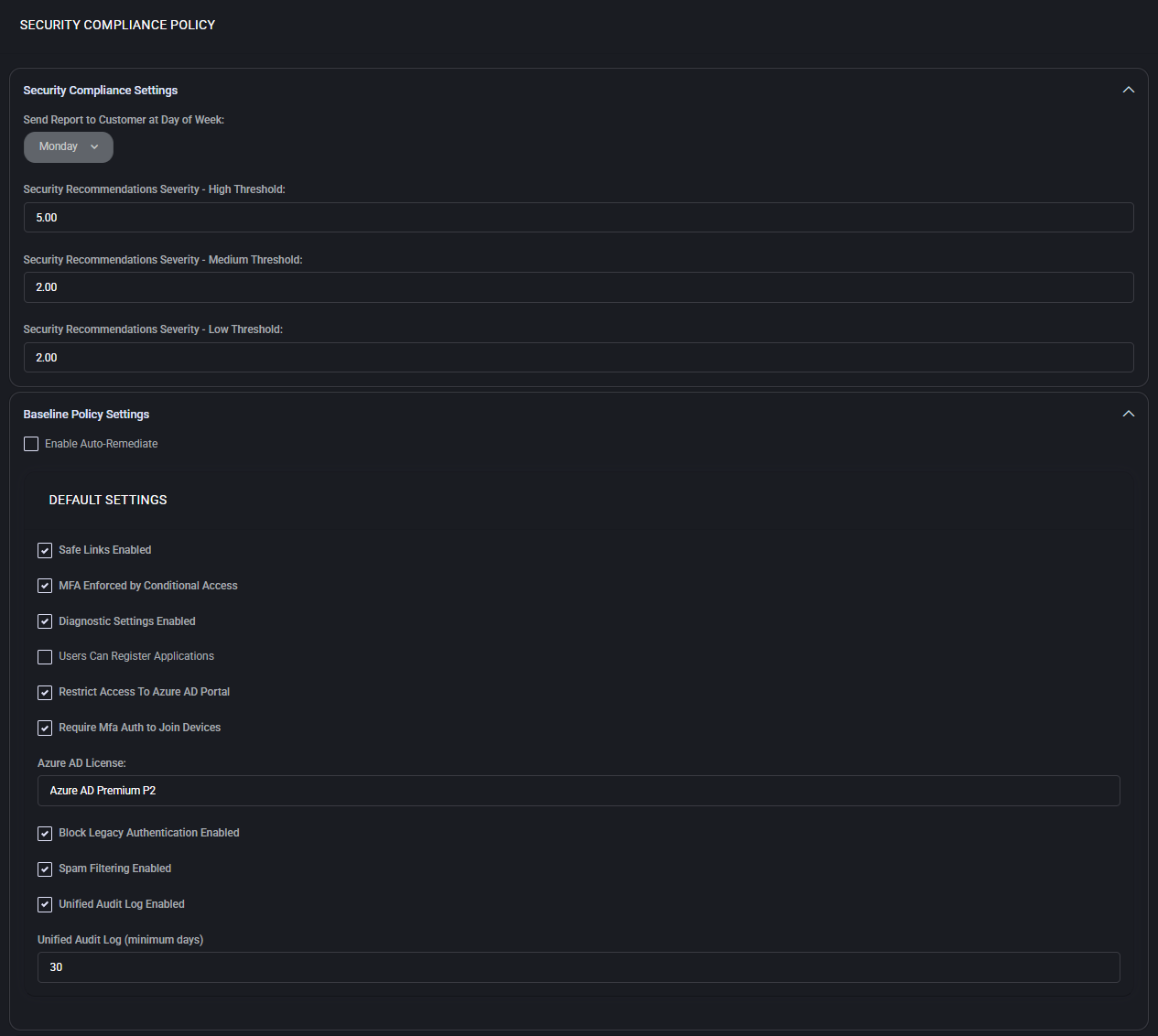
Security Compliance Settings
This section defines how often reports are sent and sets severity thresholds for recommendations.
- Send Report to Customer at Day of Week
Choose the day of the week when the security compliance report is sent to the customer. Example: Monday.
- Security Recommendations Severity – High Threshold
Set the numeric threshold (e.g., 5.00) for classifying security items as high severity. Anything above this value is considered critical.
- Security Recommendations Severity – Medium Threshold
Sets the score (e.g., 2.00) above which issues are flagged as medium severity.
- Security Recommendations Severity – Low Threshold
Minimum score (e.g., 2.00) to trigger a low severity warning or recommendation.
Baseline Policy Settings
This optional section allows enforcing baseline security settings through auto-remediation.
- Enable Auto-Remediate
When enabled, the system will automatically attempt to resolve detected misconfigurations that violate baseline rules.
The following security features can be toggled under the baseline:
- Safe Links Enabled – Protects users from malicious links by rewriting and scanning URLs in real-time.
- MFA Enforced by Conditional Access – Ensures that Multi-Factor Authentication is applied to users through conditional policies.
- Diagnostic Settings Enabled – Enables diagnostic logging for improved security event tracking.
- Users Can Register Applications – Allows or restricts user ability to register custom Azure apps.
- Restrict Access To Azure AD Portal – Prevents general access to the Azure Active Directory admin portal.
- Require MFA Auth to Join Devices – Requires MFA when users attempt to join new devices to Azure AD.
- Azure AD License – Defines the minimum required license level (e.g., Azure AD Premium P2) to enforce advanced security capabilities.
- Block Legacy Authentication Enabled – Disables insecure legacy authentication protocols.
- Spam Filtering Enabled – Enables anti-spam protection through Microsoft 365.
- Unified Audit Log Enabled – Enables a central log for auditing activity across services.
- Unified Audit Log (minimum days) – Defines the minimum retention period (e.g., 30 days) for audit logs.
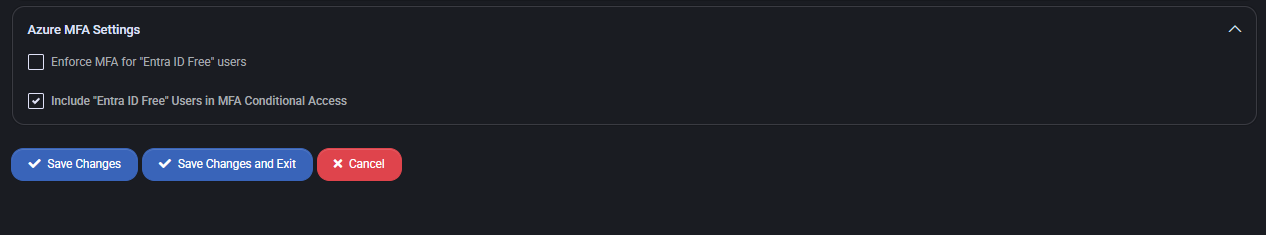
Azure MFA Settings
Controls the behavior of Multi-Factor Authentication enforcement specifically for “Entra ID Free” users.
- Enforce MFA for “Entra ID Free” users – When checked, these users must complete MFA for login.
- Include “Entra ID Free” Users in MFA Conditional Access – Ensures that conditional access rules apply to free-tier accounts.
Best Practices
- Review severity thresholds regularly to ensure they’re aligned with your organization’s risk tolerance.
- Enable auto-remediation for environments requiring strict compliance enforcement.
- Enforce MFA for all users, including “Entra ID Free,” to reduce identity-based attacks.
- Use “Azure AD Premium P2” licensing to unlock advanced conditional access and logging features.
- Schedule compliance reports on the same weekday as other maintenance activities to streamline reviews.
- Ensure “Unified Audit Log” is enabled and retained for a minimum of 30 days to support incident investigations.
Global Exchange Online Security Policy
The Global Exchange Online Security Policy provides control over the handling of URLs in email messages processed through Exchange Online. This policy specifically focuses on managing Safe Links behavior for outbound communication and internal protections.
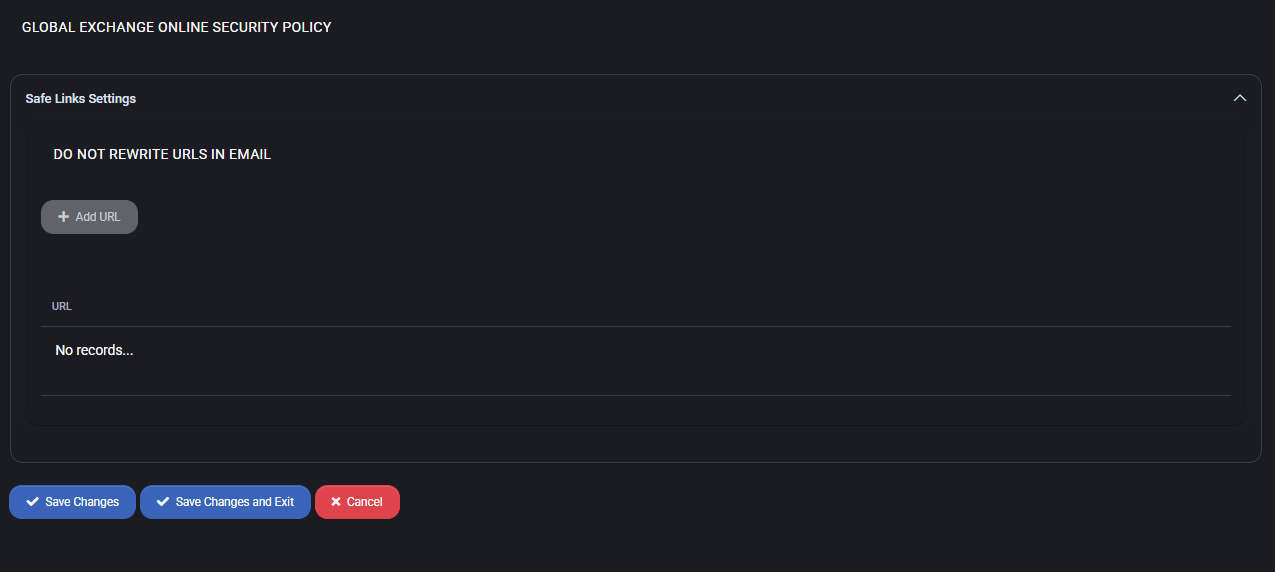
Safe Links Settings
The primary configuration in this section is the control of URL rewriting behavior in email content.
- Do Not Rewrite URLs in Email – This setting allows administrators to define exceptions for Safe Links processing. Any URL added here will be excluded from the default rewriting mechanism applied by Microsoft Defender for Office 365 (formerly ATP Safe Links).
- Add URL – Administrators can click this button to add a trusted domain or specific link to the exclusion list. This is especially useful for internal systems or services where Safe Links rewriting may break functionality.
- No Records – If no URLs are added, all links will be subject to Safe Links policies, meaning they will be rewritten and scanned by Microsoft services.
Best Practices
- Only add URLs to the exception list if rewriting causes functionality issues or false positives in trusted services.
- Regularly review the Safe Links exception list to remove outdated or deprecated URLs.
- Educate end users about the importance of Safe Links rewriting as a protection layer against phishing and malicious content.
- Use this policy in conjunction with other Microsoft 365 security tools such as Safe Attachments, anti-phishing policies, and threat intelligence reports.
- Avoid adding public URLs or third-party domains to the exception list unless absolutely necessary.



































