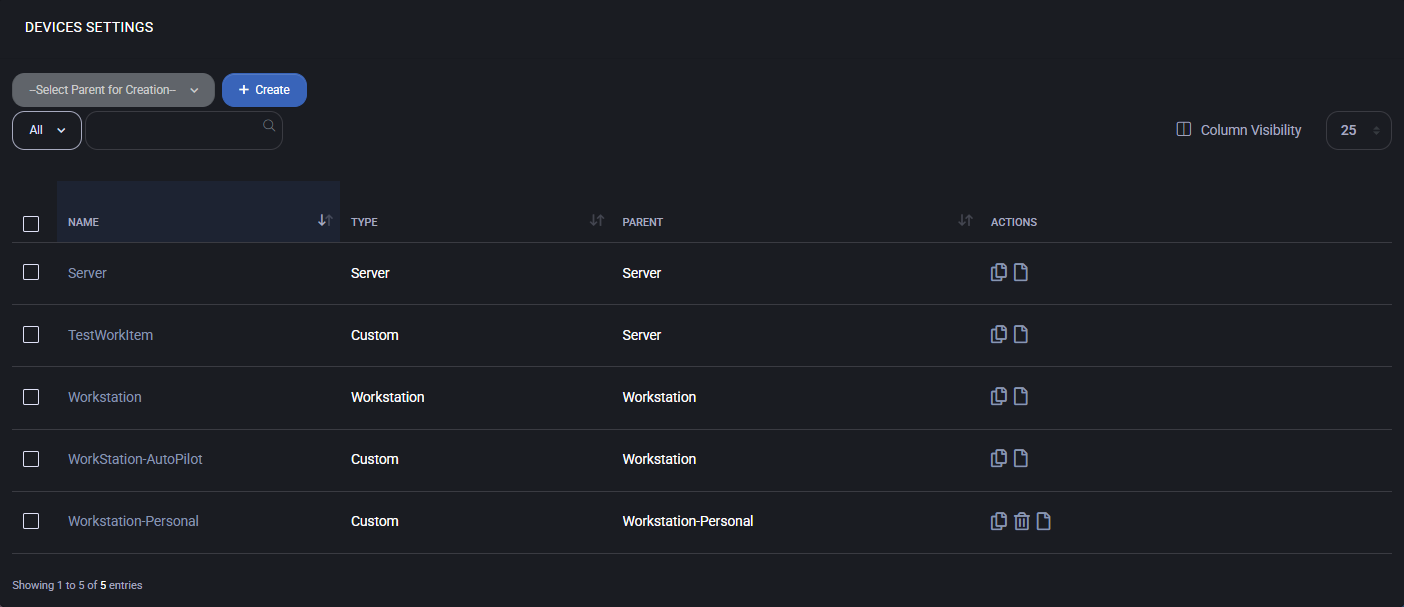
Devices Settings
The Devices Settings page in MSPControl allows you to define and manage device configuration templates used by the Autopilot. These templates can represent device types such as Servers, Workstations, or Custom categories. Each template may inherit settings from a parent, enabling consistent and automated provisioning across similar devices managed by Autopilot.
All existing templates are listed in a table with the following columns:
- Name: The name of the device setting template.
- Type: The classification of the template (e.g., Server, Workstation, or Custom).
- Parent: The template from which the current item inherits settings.
- Actions: Options to duplicate or delete the template (if applicable).
Use the dropdown above the table to select a parent group when creating a new template. Click the Create button to open the configuration interface for a new device template.
Devices Settings – Create
Clicking the Create button in the Devices Settings section opens a configuration panel with multiple tabs designed to define device behavior policies. These profiles include a wide set of system, security, update, and application-level settings that can be enforced across devices grouped under a shared configuration set. The settings are applied hierarchically and help streamline endpoint management, automation, and compliance for both workstations and servers.
The form is divided into five main tabs, each of which represents a functional group of settings applied to the target device(s).
Table of Contents – Create Tabs
Device Profile
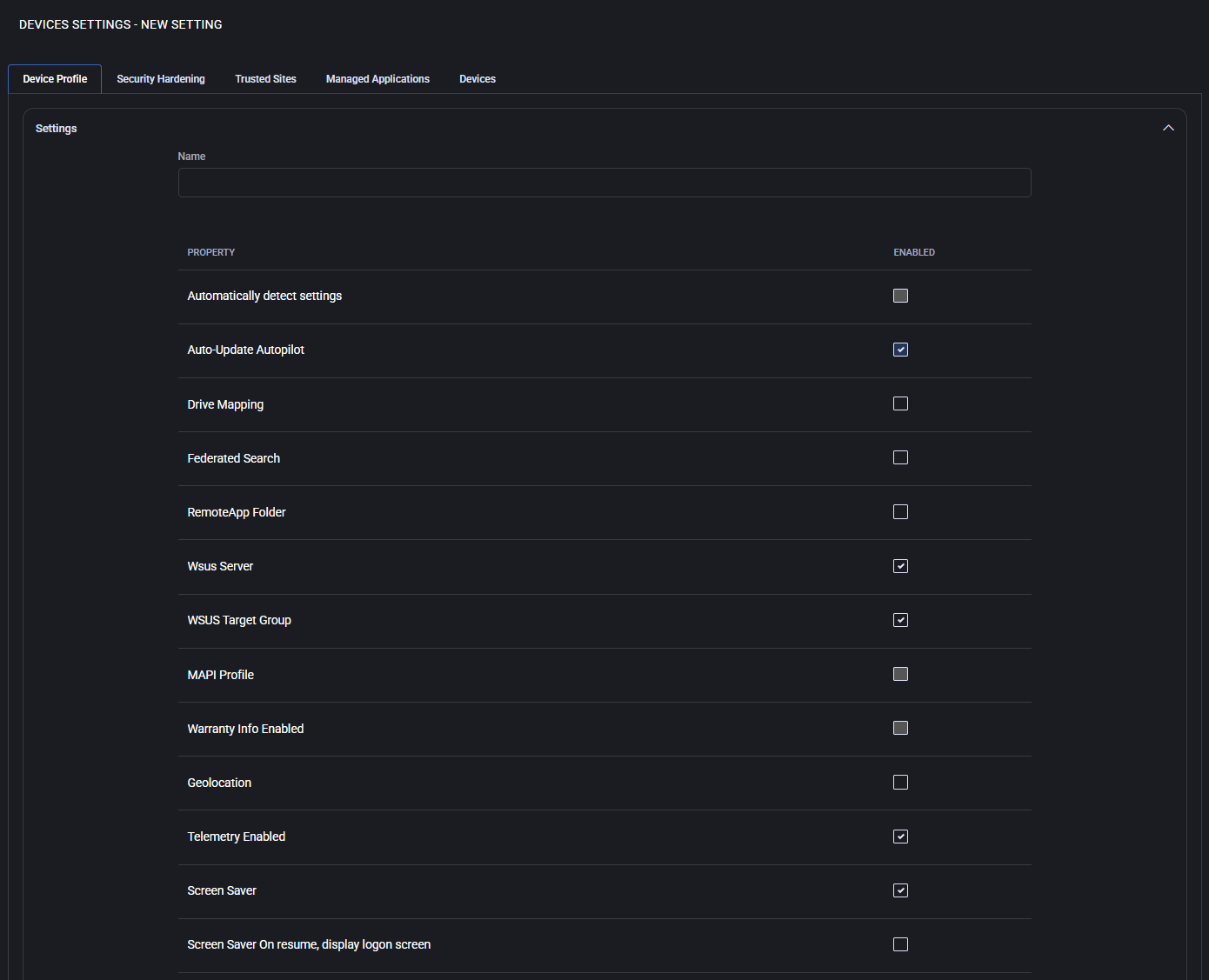
The Device Profile tab contains system-wide configuration options for devices managed by MSPControl Autopilot. These include core Windows behaviors such as automatic detection, screen saver timeout, telemetry settings, WSUS configuration, and integration with external services like Intune. These profiles define how the device behaves and integrates within the centrally managed IT environment through Autopilot.
Subsections
Settings
This section defines base-level system properties that influence both user experience and administrative behavior. Each item represents a feature that can be toggled ON or OFF per policy.
- Automatically detect settings
Enables the system to automatically detect proxy or network settings. Useful in dynamic or roaming environments where devices frequently change networks.
- Auto-Update Autopilot
Automatically updates Windows Autopilot profile settings, ensuring that devices stay aligned with the latest provisioning configurations.
- Drive Mapping
Allows configuration of network drive mappings, automatically connecting the user to shared resources such as file servers or departmental folders.
- Federated Search
Enables the use of federated search functionality, allowing Windows Search to query remote data sources or enterprise search connectors.
- RemoteApp Folder
When enabled, groups all RemoteApp shortcuts into a folder within the Start Menu or desktop environment for better organization and access.
- WSUS Server
Allows specifying a custom Windows Server Update Services (WSUS) server URL, redirecting update delivery from Microsoft’s public service to a local server for controlled patch deployment.
- WSUS Target Group
Specifies the group name that this device should belong to on the WSUS server. This allows grouping machines for staged rollouts or testing updates on specific subsets of devices.
- MAPI Profile
Enables support for Messaging Application Programming Interface (MAPI) profiles, typically used by Microsoft Outlook. Required in environments with on-premise Exchange or hybrid mail systems.
- Warranty Info Enabled
Activates retrieval of warranty data from hardware vendors (if supported), making it available in reports and device health dashboards.
- Geolocation
Allows the device to use built-in location services, such as Wi-Fi triangulation or GPS (if available), to provide geographic information to management systems.
- Telemetry Enabled
Controls whether Windows can send telemetry data to Microsoft. This setting may be needed for compliance, diagnostics, or integration with Microsoft services.
- Screen Saver
Lets you enforce a screen saver type (e.g. Blank, Bubbles, Ribbons, etc.). Can be paired with security policies for screen lock on inactivity.
- Screen Saver On resume, display logon screen
If enabled, the device will prompt for user credentials upon resuming from the screen saver, enhancing session security.
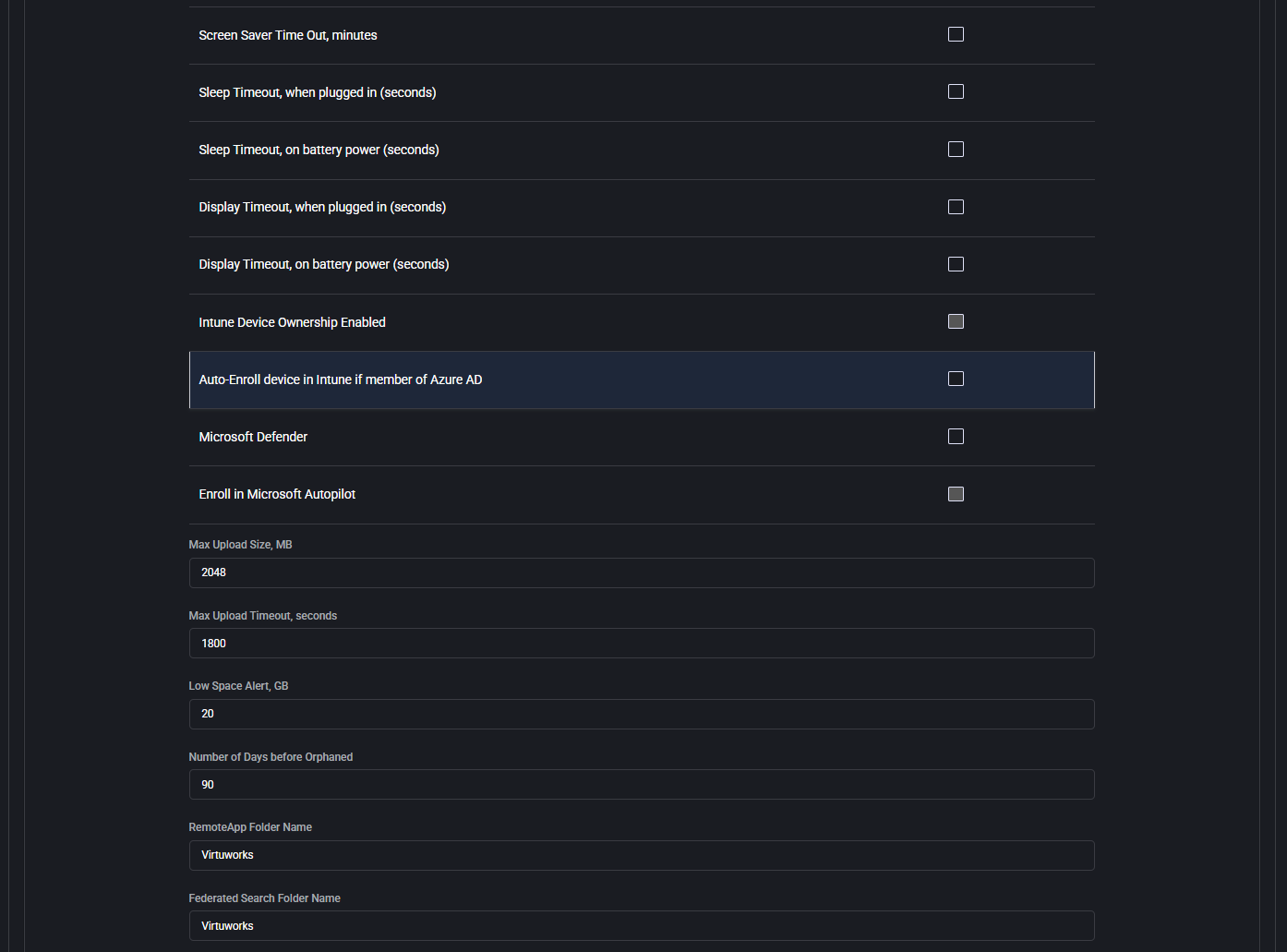
- Screen Saver Time Out, minutes
Specifies the idle time (in minutes) before the screen saver activates. Used to enforce inactivity behavior.
- Sleep Timeout, when plugged in (seconds)
Determines how long the device waits while plugged in before entering sleep mode. Set to 0 to disable.
- Sleep Timeout, on battery power (seconds)
Same as above, but applies only when running on battery. Helps conserve power in mobile scenarios.
- Display Timeout, when plugged in (seconds)
Defines when the display should turn off due to inactivity while charging or on AC power.
- Display Timeout, on battery power (seconds)
Sets display off time while running on battery, helping extend battery life.
- Intune Device Ownership Enabled
Enables the system to assign device ownership in Microsoft Intune. Used in corporate-managed environments.
- Auto-Enroll device in Intune if member of Azure AD
Automates device enrollment in Microsoft Intune if the device is joined to Azure Active Directory. Ensures policy compliance without user intervention.
- Microsoft Defender
Enables or disables Microsoft Defender antivirus protection. This can be managed centrally for environments with third-party security solutions.
- Enroll in Microsoft Autopilot
Enrolls the device into Microsoft Autopilot for automated provisioning and zero-touch deployment. Recommended for standardizing device setup workflows.
- Max Upload Size, MB
Sets the maximum allowed upload size in megabytes for operations like logs, diagnostics, or file transfers through the agent.
- Max Upload Timeout, seconds
Defines the time limit (in seconds) for upload operations before timing out.
- Low Space Alert, GB
Sets a threshold (in gigabytes) below which the system will generate alerts about low disk space.
- Number of Days before Orphaned
Defines how many days a device can remain inactive or unlinked before being flagged as orphaned for further review or cleanup.
- RemoteApp Folder Name
Specifies the name of the folder where RemoteApp shortcuts will be placed. Helps organize access to remote apps in the user interface.
- Federated Search Folder Name
Names the folder used to group federated search resources, improving visibility and categorization for users.
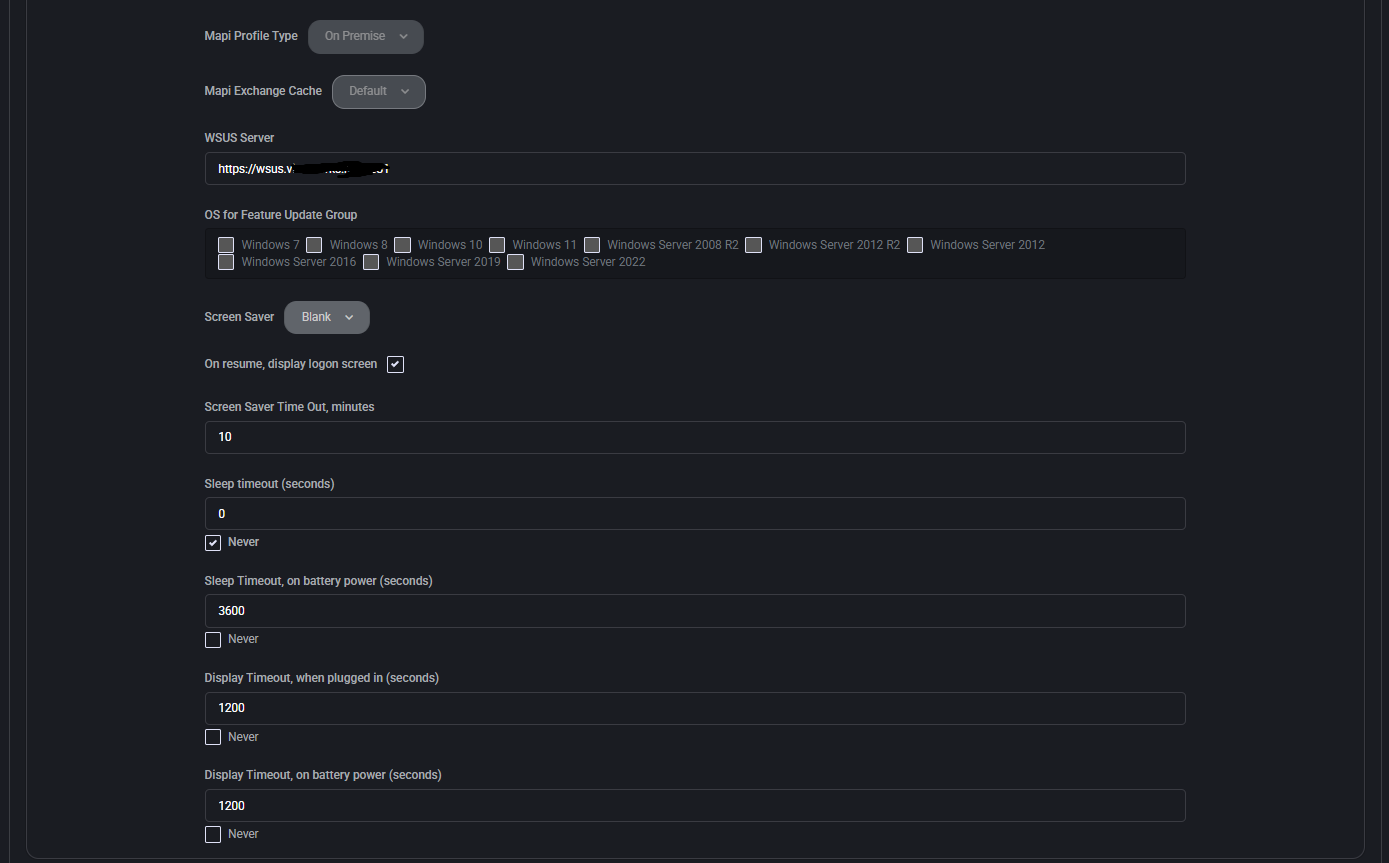
- MAPI Profile Type
Defines whether the Messaging Application Programming Interface (MAPI) profile is configured for On Premise or Hosted Exchange environments. This affects how mail clients interact with the Exchange server.
- MAPI Exchange Cache
Determines the cache mode for Outlook clients using MAPI. Options may include Default, Enabled, or Disabled.
- WSUS Server
Specifies the URL of the Windows Server Update Services (WSUS) server. Devices will use this path to receive Windows updates.
- OS for Feature Update Group
Allows selecting specific Windows OS versions that are targeted for feature updates. This enables granular update control across various device types.
- Screen Saver
Sets the screen saver behavior. Options may include None, Blank, or custom modes to align with organizational policies.
- On resume, display logon screen
When enabled, users must authenticate after screen saver deactivates, enhancing security.
Windows Update Settings
This section allows administrators to define how Windows Updates are handled on managed devices, including scheduling, reboot behavior, source policies, and notification options. Fine-tuning these settings ensures compliance, reduces disruptions, and aligns update delivery with organizational requirements.
- Auto Update Enabled
Enables or disables Windows Updates on the device. When disabled, no update checks or installations are performed.
- Auto Update Options
Specifies how updates are handled. Options may include automatic download and installation, notify only, or schedule-based control.
- Scheduled Install Day
Defines the specific day of the week when scheduled updates should be installed. Helps enforce a consistent maintenance window.
- Scheduled Install Time
Sets the exact time (e.g. 2 AM) at which scheduled installations will begin. Devices will attempt to apply updates during this window.
- Auto Reboot With Logged On Users
When enabled, the device will reboot automatically after updates even if users are currently logged in.
- Always automatically restart at the scheduled time
Forces the device to restart regardless of user activity if the scheduled time is reached.
- Always automatically restart at the scheduled time timeout (minutes)
Sets a delay (in minutes) after which the device restarts if updates require it and the scheduled time has passed.
- Include Recommended Updates
Ensures optional recommended updates are included along with important ones during the update process.
- Install updates for other Microsoft products
Extends Windows Update to include Microsoft Office, Visual Studio, and other non-OS products.
- Show a notification when your PC requires a restart to finish updating
Displays a system tray alert or pop-up when updates are pending a reboot, ensuring the user is informed.
- Notification dismissal method
Controls how update notifications are dismissed — automatically, manually, or based on policy settings.
- Enable Active Hours
When enabled, defines a daily time window during which reboots for updates are not permitted to avoid disrupting users.
- Active Hours Start
Start of the protected time window where automatic restarts will be blocked.
- Active Hours End
End of the protected time window where automatic restarts will be blocked.
- SLA for Number of Days
Defines the maximum number of days allowed before updates must be installed to remain within service level agreements.
- Check OS Version for Servicing Support
Validates whether the current Windows version is eligible for update servicing, blocking updates on unsupported builds.
- Use Update Class Policy Source
Applies group policy-defined settings to control update classifications (e.g., critical, security, feature).
- Set Policy Driven Update Source For Feature Updates
Overrides the default update source with a policy-defined location specifically for feature updates.
- Set Policy Driven Update Source For Quality Updates
Overrides the update source for cumulative or monthly quality updates, typically for patch management.
- Set Policy Driven Update Source For Driver Updates
Applies a specific update source for hardware drivers, enabling integration with custom driver repositories.
- Set Policy Driven Update Source For Other Updates
Defines the update source for miscellaneous categories outside of core OS, quality, or drivers.
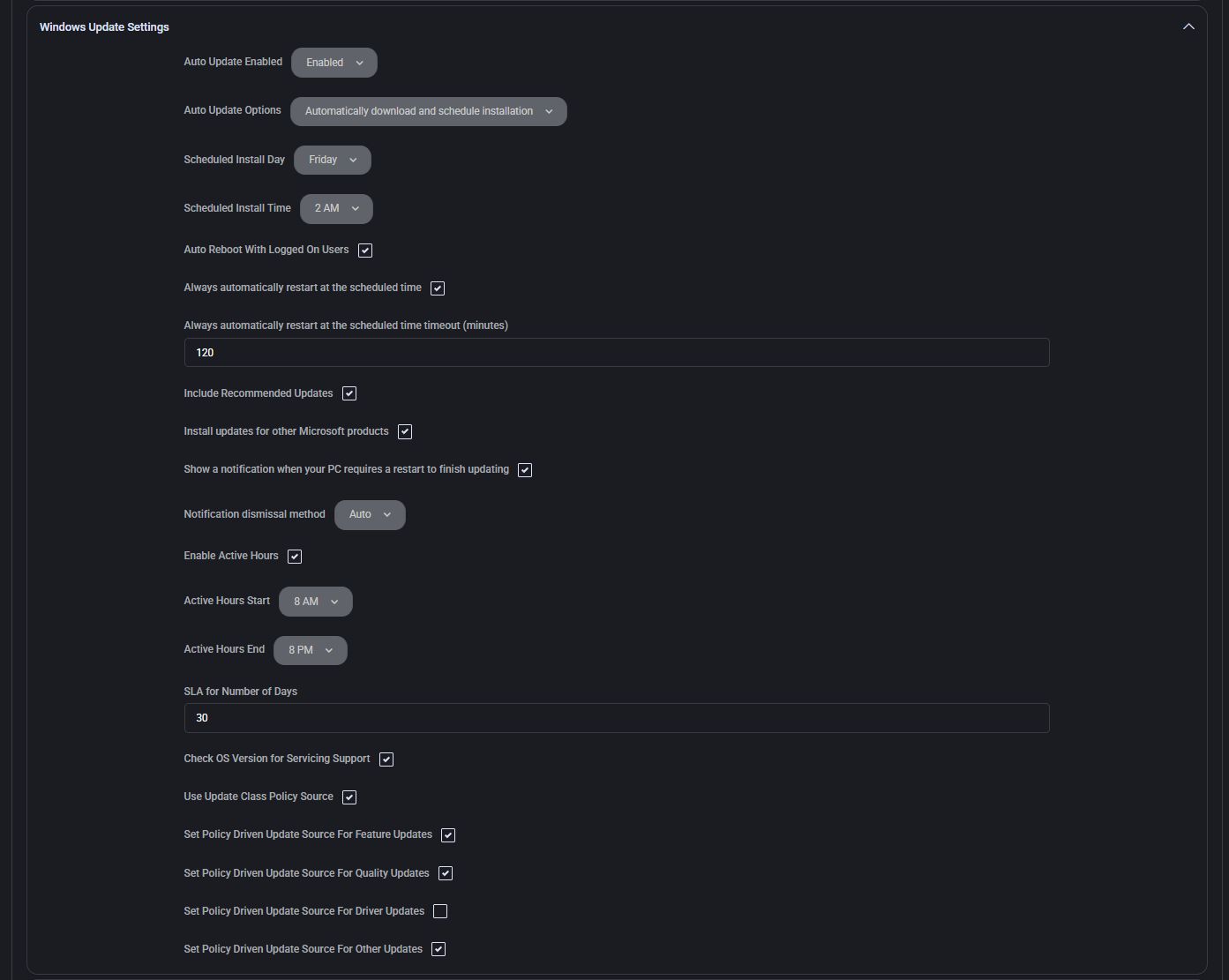
Third Party Patching
This section allows configuration of patch management for third-party applications. These settings determine when and how non-Microsoft software updates are executed, ensuring broader security compliance beyond the Windows ecosystem.
- AutoRun
Defines whether the patching process runs automatically. Can be set to Enabled or Disabled.
- Run Task
Specifies the recurrence of the patching task. Options include Daily, Weekly, or other intervals.
- Day of Week
When Weekly is selected, defines the specific weekday (e.g., Thursday) when the patch task is triggered.
- Start Time
Indicates the time of day when the patching task begins (e.g., 08:00 PM).
- Auto Reboot With Logged On Users
When enabled, allows the system to reboot automatically after patching, even if users are currently logged in.
- Show a notification when your PC requires a restart to finish updating
Displays a user notification if a reboot is needed to complete the third-party patch process.
- Run updates under user context
Executes the patching task within the current user’s security context, typically required for interactive or user-specific application updates.
- Only when user is local Administrator
Restricts patch execution to scenarios where the current user holds local administrator rights. This is a security precaution to avoid privilege elevation issues.
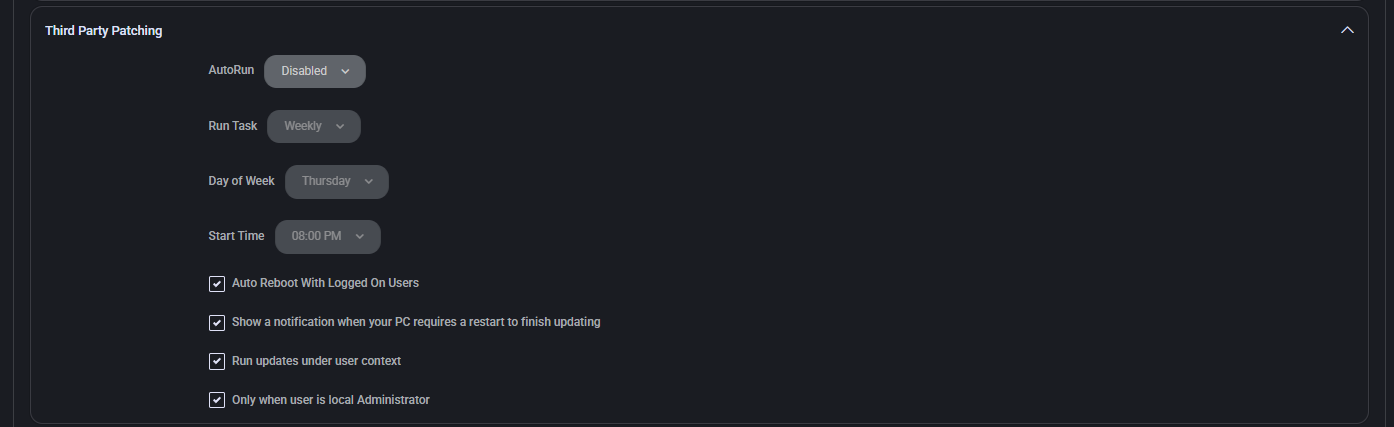
Intune
This section manages Microsoft Intune enrollment behavior. It determines ownership type and location-based policies for automatic device enrollment into Intune, supporting streamlined management in corporate and hybrid environments.
- Device Ownership
Specifies whether the device is considered Corporate or Personal. This setting influences policy enforcement and available management features in Intune.
- Auto-Enroll in Intune (Device Locations)
Defines which device locations will automatically trigger enrollment into Intune:
- All locations — All devices, regardless of location, will be enrolled.
- Selected locations — Only devices in designated locations will be enrolled.
- None — Auto-enrollment is disabled for all locations.
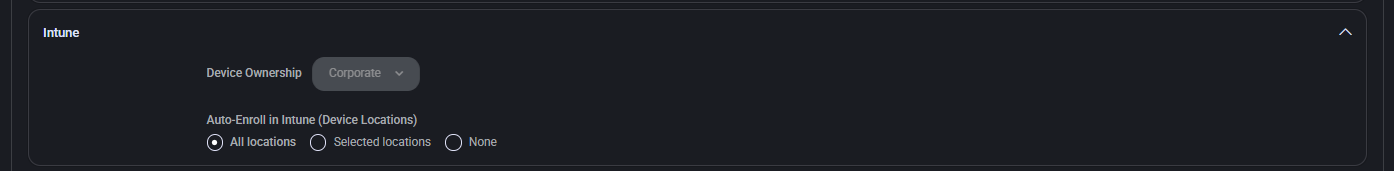
Windows Disk Cleanup
This section defines the automated cleanup behavior for Windows system files. It allows scheduling regular cleanups and selecting specific file categories to delete, helping free up disk space and maintain system performance.
- AutoRun
Specifies whether the cleanup task is automatically executed. Options include Disabled, Enabled.
- Run Task
Determines task frequency, such as Weekly or Daily.
- Day of Week
Select the day when cleanup should be performed.
- Start Time
Specifies the time of day when the cleanup task should begin.
Cleanup File Types:
- Temporary Setup Files
- Setup Log Files
- Diagnostic Data Viewer Database Files
- Temporary Internet Files
- System Error Minidump Files
- Branch Cache
- Delivery Optimization Files
- Recycle Bin
- Temporary Files
- User File History
- Downloads (Personal downloads folder)
- Windows Upgrade Log Files
- Old Chkdsk Files
- Microsoft Defender Antivirus
- Downloaded Program Files
- System Error Memory Dump Files
- Windows Error Reports and Feedback Diagnostics
- DirectX Shader Cache
- Language Resources Files
- Retail Demo Offline Content
- Thumbnails
- Catalog Files for the Content Indexer
- Offline Files
- Windows Update Cleanup
Device Local Admin
This section allows you to define local administrator settings for devices, including credential rotation for enhanced security. You can create a static or rotating local admin account as part of the deployment policy.
- Device Local Admin
Enables or disables the creation and management of a local administrator account on the device.
- Local Admin Username
Defines the username for the local admin account that will be provisioned.
- Auto-Rotate Local Admin Password
If enabled, the local admin password will be automatically rotated at a defined interval.
- Interval to Auto-Rotate Local Admin Password (Days)
Specifies how often (in days) the local admin password should be changed if auto-rotation is enabled.
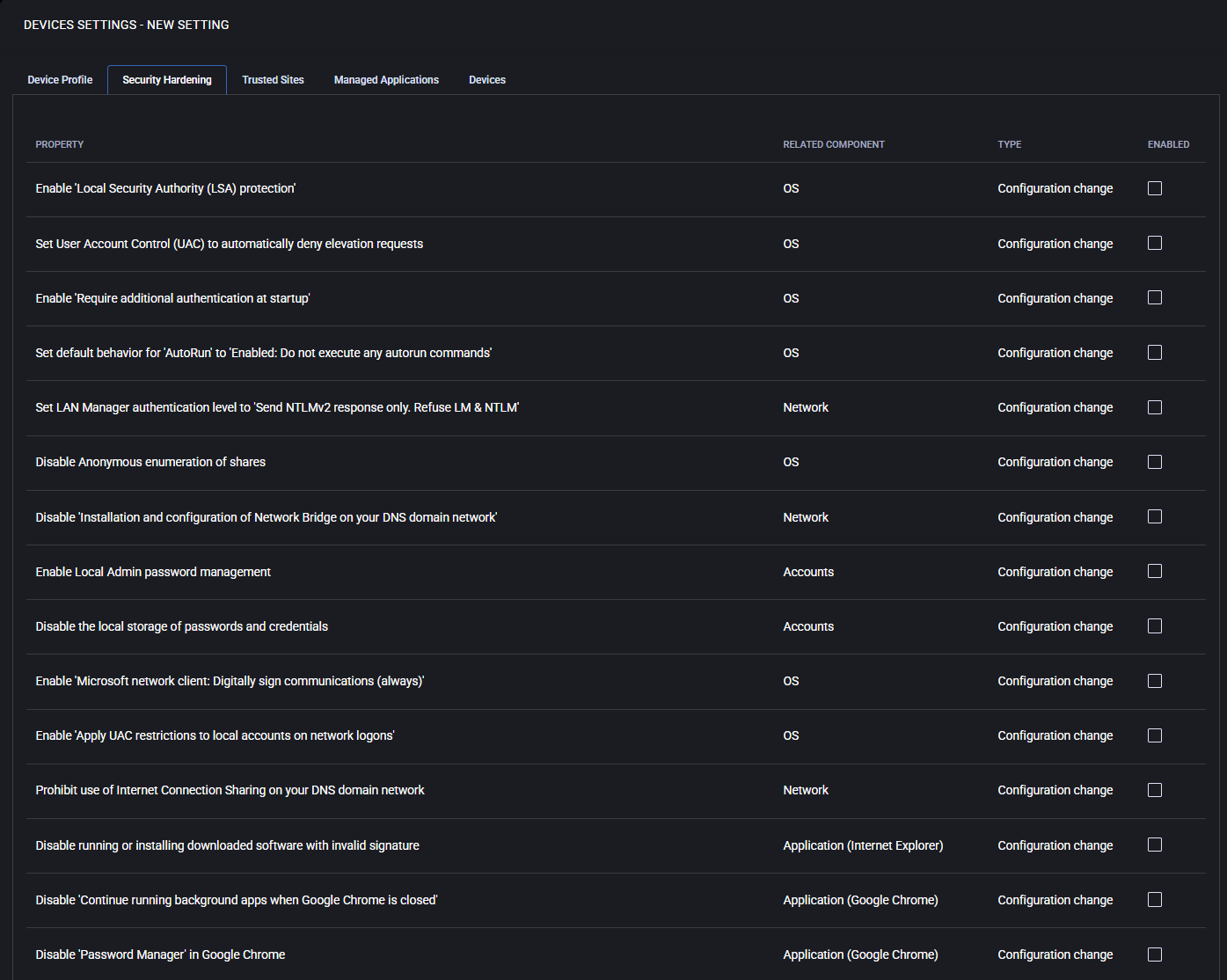
Security Hardening
This section includes predefined system-level hardening policies designed to enhance device security by disabling legacy protocols, enforcing secure authentication, and restricting potentially insecure behaviors. Each setting can be selectively enabled based on your organization’s compliance requirements.
- Enable ‘Local Security Authority (LSA) protection’:
Protects the LSASS process from unauthorized code injection, reducing credential theft risks.
- Set User Account Control (UAC) to automatically deny elevation requests:
Prevents automatic privilege elevation, adding an extra layer of defense.
- Enable ‘Require additional authentication at startup’:
Requires authentication (e.g., BitLocker PIN) before boot, protecting data at rest.
- Set default behavior for ‘AutoRun’ to ‘Enabled: Do not execute any autorun commands’:
Disables AutoRun commands to block potential malware execution from USB or network drives.
- Set LAN Manager authentication level to ‘Send NTLMv2 response only. Refuse LM & NTLM’:
Enforces stronger authentication standards, rejecting older, insecure protocols.
- Disable Anonymous enumeration of shares:
Prevents unauthenticated users from discovering shared folders.
- Disable ‘Installation and configuration of Network Bridge on your DNS domain network’:
Blocks users from bridging network adapters, reducing lateral attack risks.
- Enable Local Admin password management:
Allows secure, automatic rotation of local administrator passwords.
- Disable the local storage of passwords and credentials:
Prevents Windows from caching login data, lowering offline attack surface.
- Enable ‘Microsoft network client: Digitally sign communications (always)’:
Ensures SMB communications are signed to prevent tampering.
- Enable ‘Apply UAC restrictions to local accounts on network logons’:
Limits local admin privileges when logging in over the network.
- Prohibit use of Internet Connection Sharing on your DNS domain network:
Prevents users from creating unauthorized shared connections.
- Disable running or installing downloaded software with invalid signature:
Blocks execution of software that fails digital signature validation, improving endpoint security.
- Disable ‘Continue running background apps when Google Chrome is closed’:
Prevents Chrome from continuing to run after closure, saving resources and reducing attack vectors.
- Disable ‘Password Manager’ in Google Chrome:
Prevents Chrome from saving and autofilling passwords, enforcing use of enterprise-grade solutions.
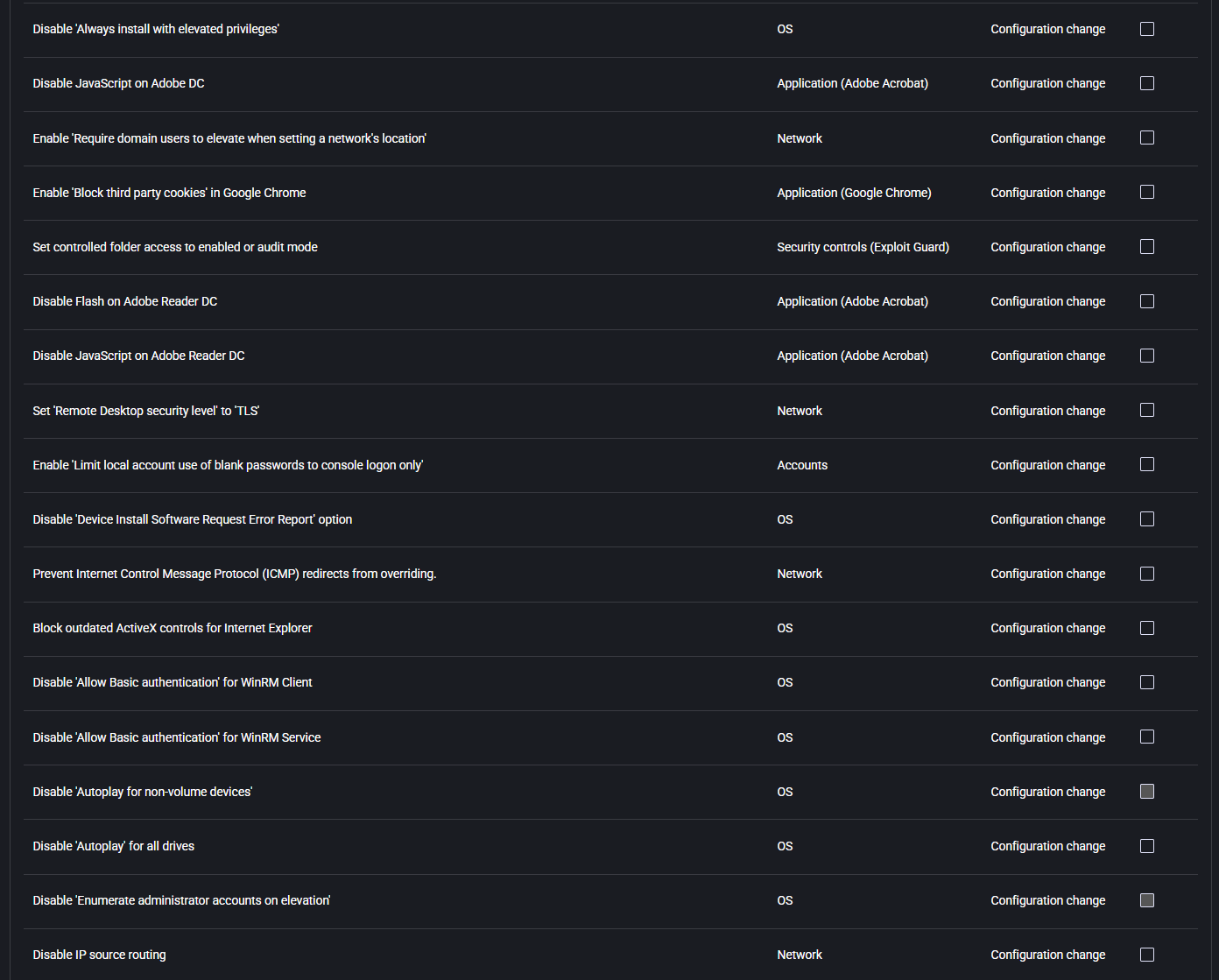
- Disable ‘Always install with elevated privileges’:
Prevents software installations from running with administrative rights unless explicitly allowed, reducing privilege escalation risks.
- Disable JavaScript on Adobe DC:
Disables scripting capabilities in Adobe Acrobat, mitigating risk from malicious PDFs.
- Enable ‘Require domain users to elevate when setting a network’s location’:
Ensures users need elevated rights to define whether a network is public, private, or domain — helping prevent exposure.
- Enable ‘Block third party cookies’ in Google Chrome:
Prevents unauthorized tracking across sites, improving browser privacy and security.
- Set controlled folder access to enabled or audit mode:
Protects key system folders from ransomware and unauthorized changes by enabling Controlled Folder Access via Microsoft Defender Exploit Guard.
- Disable Flash on Adobe Reader DC:
Prevents use of deprecated Flash components in Adobe, reducing exposure to vulnerabilities.
- Disable JavaScript on Adobe Reader DC:
Similar to Acrobat DC, disables scripting in Reader to reduce attack surface.
- Set ‘Remote Desktop security level’ to ‘TLS’:
Forces TLS encryption for RDP sessions, replacing weaker security methods.
- Enable ‘Limit local account use of blank passwords to console logon only’:
Prevents remote or network logins with accounts that have blank passwords.
- Disable ‘Device Install Software Request Error Report’ option:
Stops Windows from sending error data when device installations fail — minimizing information leaks.
- Prevent Internet Control Message Protocol (ICMP) redirects from overriding:
Hardens routing table protection by blocking ICMP-based route changes.
- Block outdated ActiveX controls for Internet Explorer:
Prevents use of legacy ActiveX components that are often targeted in exploits.
- Disable ‘Allow Basic authentication’ for WinRM Client:
Blocks basic (plaintext) authentication for remote management via WinRM client.
- Disable ‘Allow Basic authentication’ for WinRM Service:
Prevents WinRM services from accepting Basic auth, enforcing more secure mechanisms like Kerberos or certificate-based authentication.
- Disable ‘Autoplay’ for non-volume devices:
Disables automatic content execution from removable media like USB sticks, reducing malware risks.
- Disable ‘Autoplay’ for all drives:
Enforces a system-wide block on automatic execution from any drive type.
- Disable ‘Enumerate administrator accounts on elevation’:
Prevents listing of admin accounts when a non-admin user triggers a UAC prompt, hiding internal usernames.
- Disable IP source routing:
Blocks use of source routing, which can be abused for spoofing and routing-based attacks.
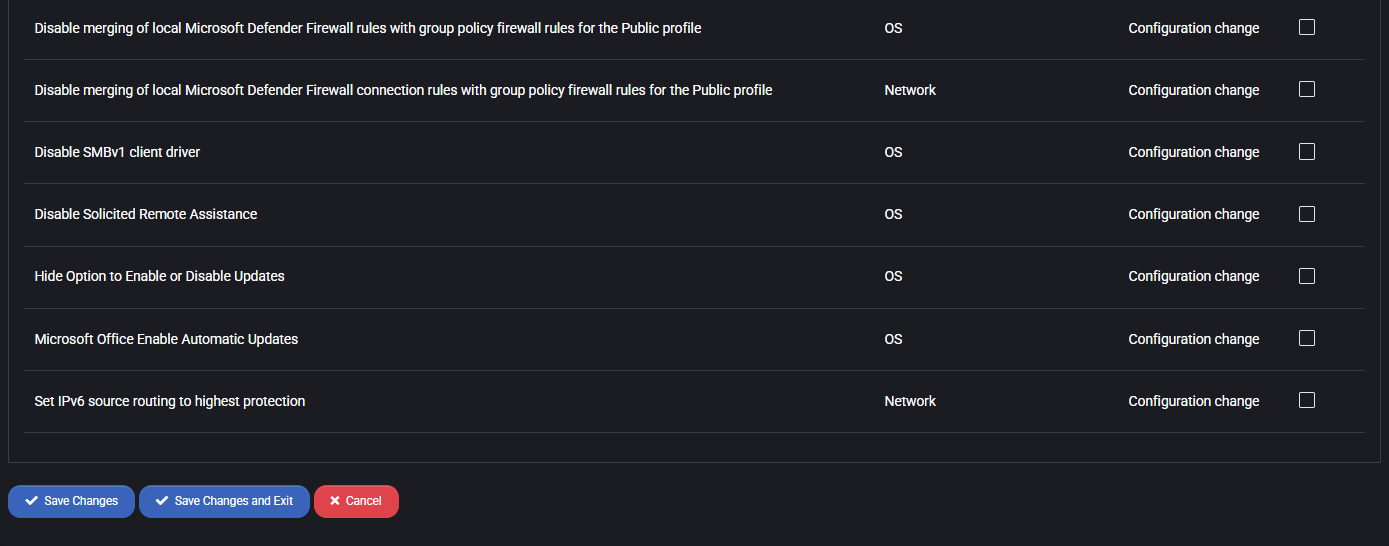
- Disable merging of local Microsoft Defender Firewall rules with group policy firewall rules for the Public profile:
Prevents local firewall exceptions from overriding stricter group policy rules, increasing policy enforcement.
- Disable merging of local Microsoft Defender Firewall connection rules with group policy firewall rules for the Public profile:
Similar to above, but applies to connection rules specifically. Helps ensure consistency in policy-controlled environments.
- Disable SMBv1 client driver:
Disables legacy SMBv1 protocol which is outdated and insecure, mitigating risks like WannaCry attacks.
- Disable Solicited Remote Assistance:
Prevents users from requesting remote assistance sessions, which may be exploited if misconfigured.
- Hide Option to Enable or Disable Updates:
Removes access to toggle update preferences, enforcing update policy compliance.
- Microsoft Office Enable Automatic Updates:
Ensures that Office apps receive critical updates automatically for security and stability.
- Set IPv6 source routing to highest protection:
Prevents IPv6 source routing, which can be exploited to bypass normal routing and security rules.
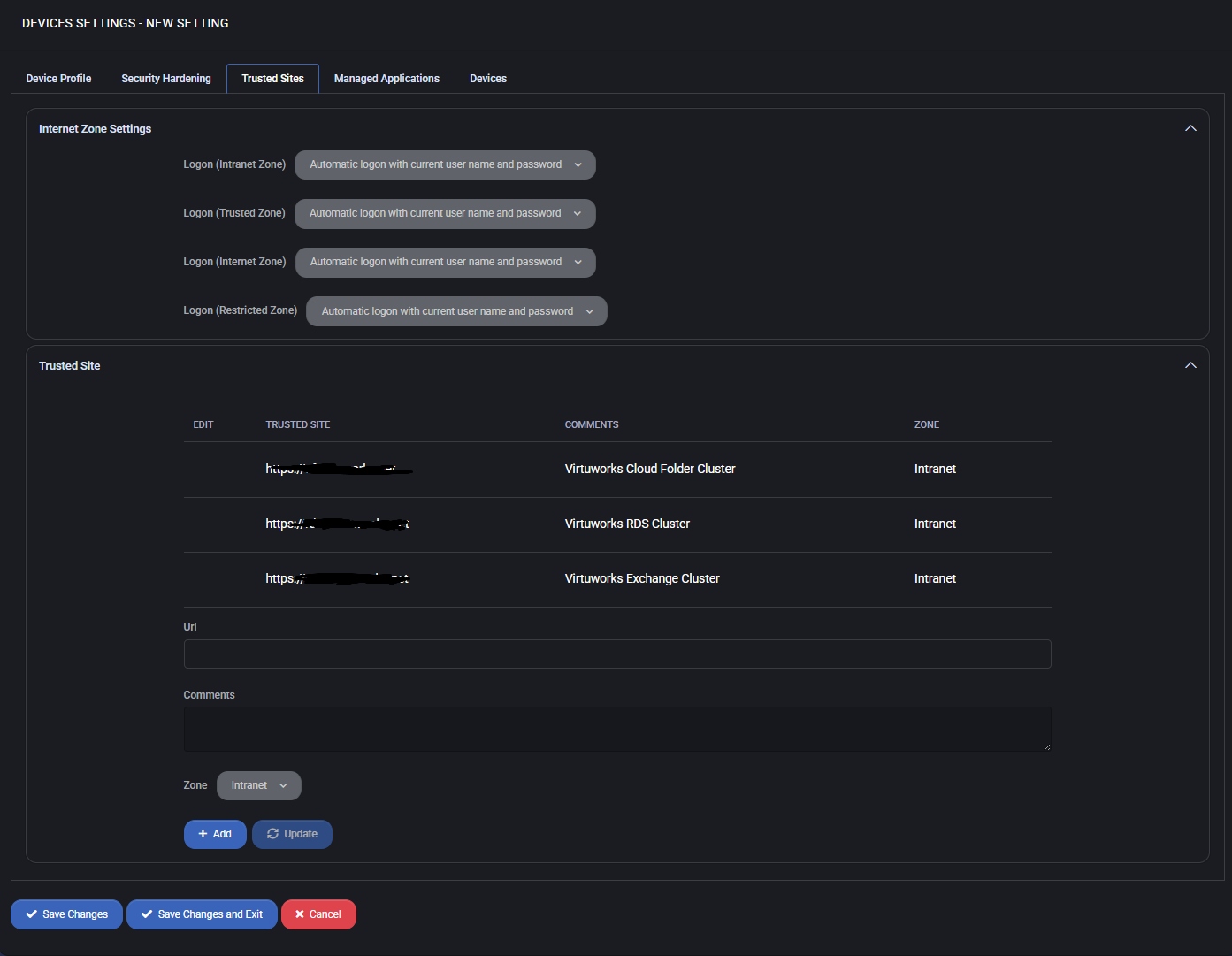
Trusted Sites
This section allows you to configure zone-based logon behavior and define a list of trusted websites for devices managed via MSPControl Autopilot. These settings ensure that your managed machines correctly authenticate with internal resources and cloud services based on their zone classification.
Internet Zone Settings
Use the dropdown menus to control how devices authenticate in different Internet Explorer security zones:
- Logon (Intranet Zone): Set authentication method for local network resources.
- Logon (Trusted Zone): Define how logins are handled for manually specified trusted sites.
- Logon (Internet Zone): Manage how standard internet sites should be authenticated.
- Logon (Restricted Zone): Define login behavior for potentially unsafe or limited-access sites.
Trusted Site List
Add URLs that should be treated as trusted by the browser and OS-level authentication mechanisms. Each entry can be assigned a zone (e.g., Intranet) and a descriptive comment for administrative clarity.
The table displays configured trusted sites along with their assigned zones and optional comments. You can add new entries or edit existing ones using the form below.
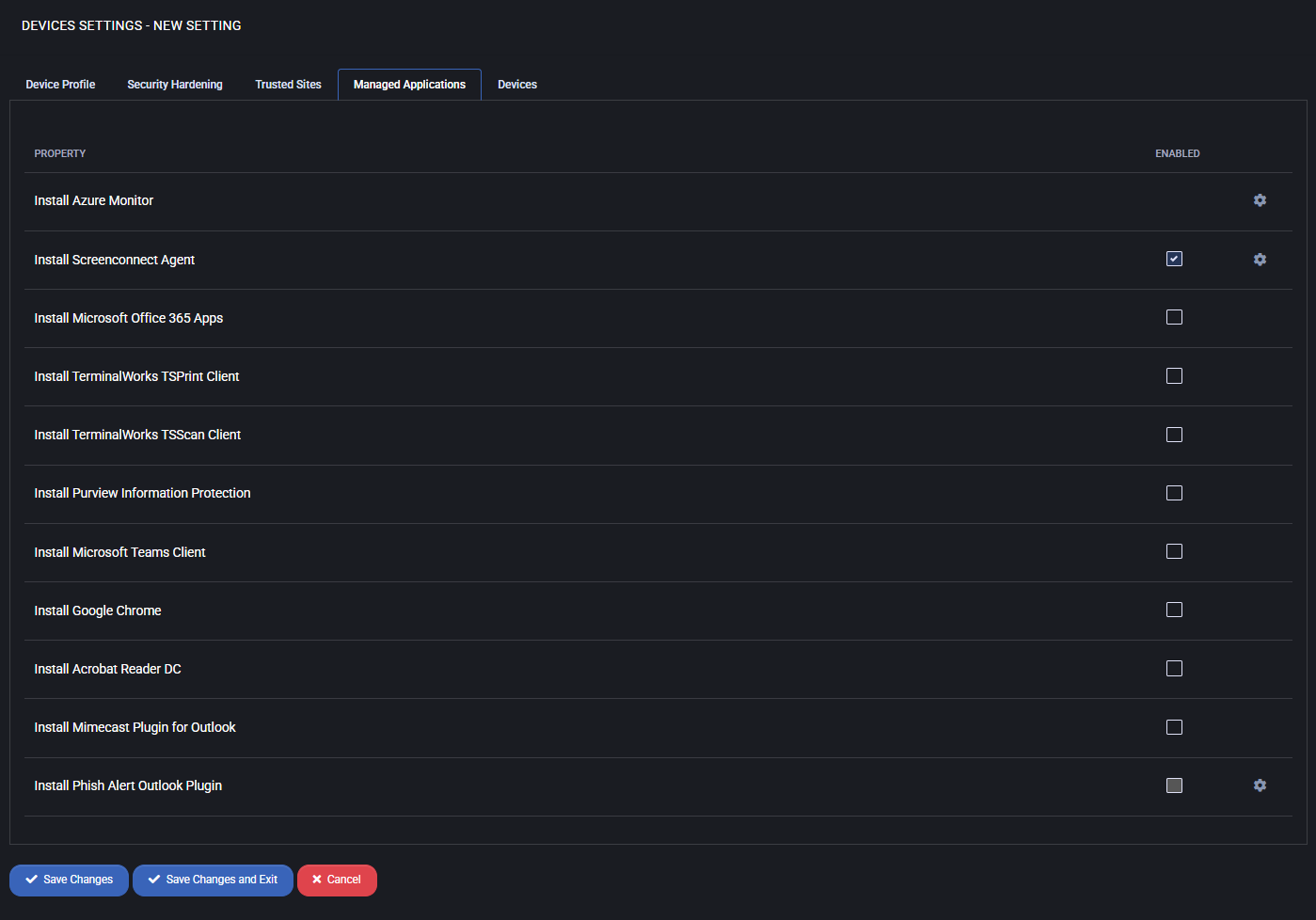
Managed Applications
This section allows you to define which applications should be automatically installed on devices managed via MSPControl Autopilot. These options ensure that critical software is consistently deployed across your organization’s infrastructure, improving security, productivity, and standardization.
- Install Azure Monitor: Enables installation of Microsoft Azure Monitor agent to collect performance and diagnostic data.
- Install Screenconnect Agent: Deploys the remote access agent for support and administration.
- Install Microsoft Office 365 Apps: Automates deployment of Microsoft 365 productivity suite.
- Install TerminalWorks TSPrint Client: Installs TSPrint for remote desktop printing functionality.
- Install TerminalWorks TSScan Client: Installs TSScan for remote desktop scanning capabilities.
- Install Purview Information Protection: Adds Microsoft Purview tools for data protection and compliance.
- Install Microsoft Teams Client: Installs Microsoft Teams for communication and collaboration.
- Install Google Chrome: Deploys Google Chrome as the primary or secondary web browser.
- Install Acrobat Reader DC: Installs Adobe Reader for viewing PDF documents.
- Install Mimecast Plugin for Outlook: Adds email security and archiving plugin for Outlook users.
- Install Phish Alert Outlook Plugin: Installs the KnowBe4 plugin allowing users to report suspicious emails directly from Outlook.
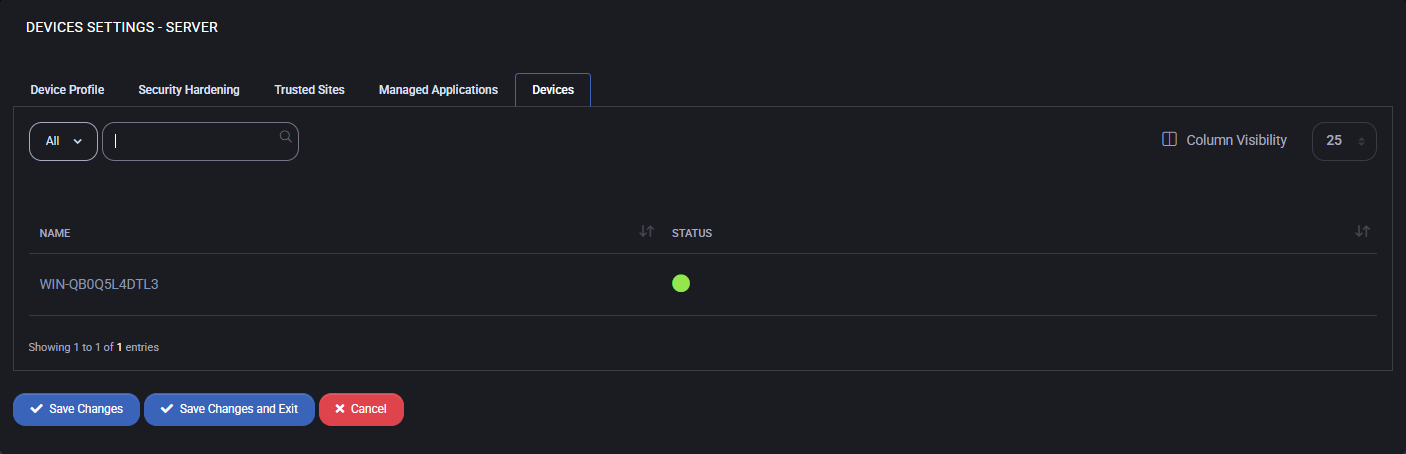
Devices
This tab displays the list of endpoints currently associated with the selected Device Settings template. These are physical or virtual machines running the MSPControl Autopilot agent and actively using the configuration profile. The list includes the device name and its connection status. When creating a new template, this tab will be empty. Once the profile is assigned and applied to devices, they will appear here for tracking and management purposes.
Best Practices
- Plan your configuration hierarchy: Use parent-child templates to enforce consistent baseline settings while allowing targeted overrides for specific device types (e.g. Workstations vs Servers).
- Start from a minimal baseline: Begin with essential settings only and expand gradually. Over-configuring from the start can lead to conflicts or unintended behavior.
- Use descriptive template names: Clearly name each Device Settings template to reflect its purpose or assigned department, making management easier as your device fleet grows.
- Leverage Security Hardening: Enable configuration changes that align with cybersecurity standards (e.g. CIS Benchmarks, NIST) to enhance endpoint protection with minimal overhead.
- Standardize Trusted Sites and Zones: Configure authentication policies and allowed intranet URLs centrally to reduce user prompts and avoid misconfigurations.
- Automate Application Deployment: Pre-select critical apps under the Managed Applications tab to ensure devices are provisioned consistently with required tools and security plugins.
- Monitor device status: Regularly check the Devices tab to verify whether your templates are correctly applied and agents are online. Investigate missing or offline devices promptly.
- Document exceptions: If certain machines require deviation from the standard template (e.g. different security rules or trusted sites), document the rationale and create a cloned template to isolate the change.
- Test before production rollout: Assign new or modified templates to a small test group of devices first. Validate results before wide deployment to avoid service disruptions.
- Review and update periodically: As software evolves and new threats emerge, revisit your hardening rules, application list, and policies at least quarterly.

















